


Back to resources
How Britive Can Add Critical Value to Your Lacework Investment
April 2021 / 6 min. read /

As cloud computing and DevOps gained momentum in recent years, many in the IT security community began to see rapidly widening gaps between the needs of enterprises building innovative digital services in the cloud and the limitations of traditional security solutions designed for data centers. The founders of Britive were among these observers. Their collective vision was to create a dynamic and intelligent solution to help companies with privileged access protection in multi-cloud environments. The Britive platform was the result: a multi-cloud native offering that centralizes access management across the entire landscape of cloud platforms and apps, in addition to policy enforcement and threat monitoring.
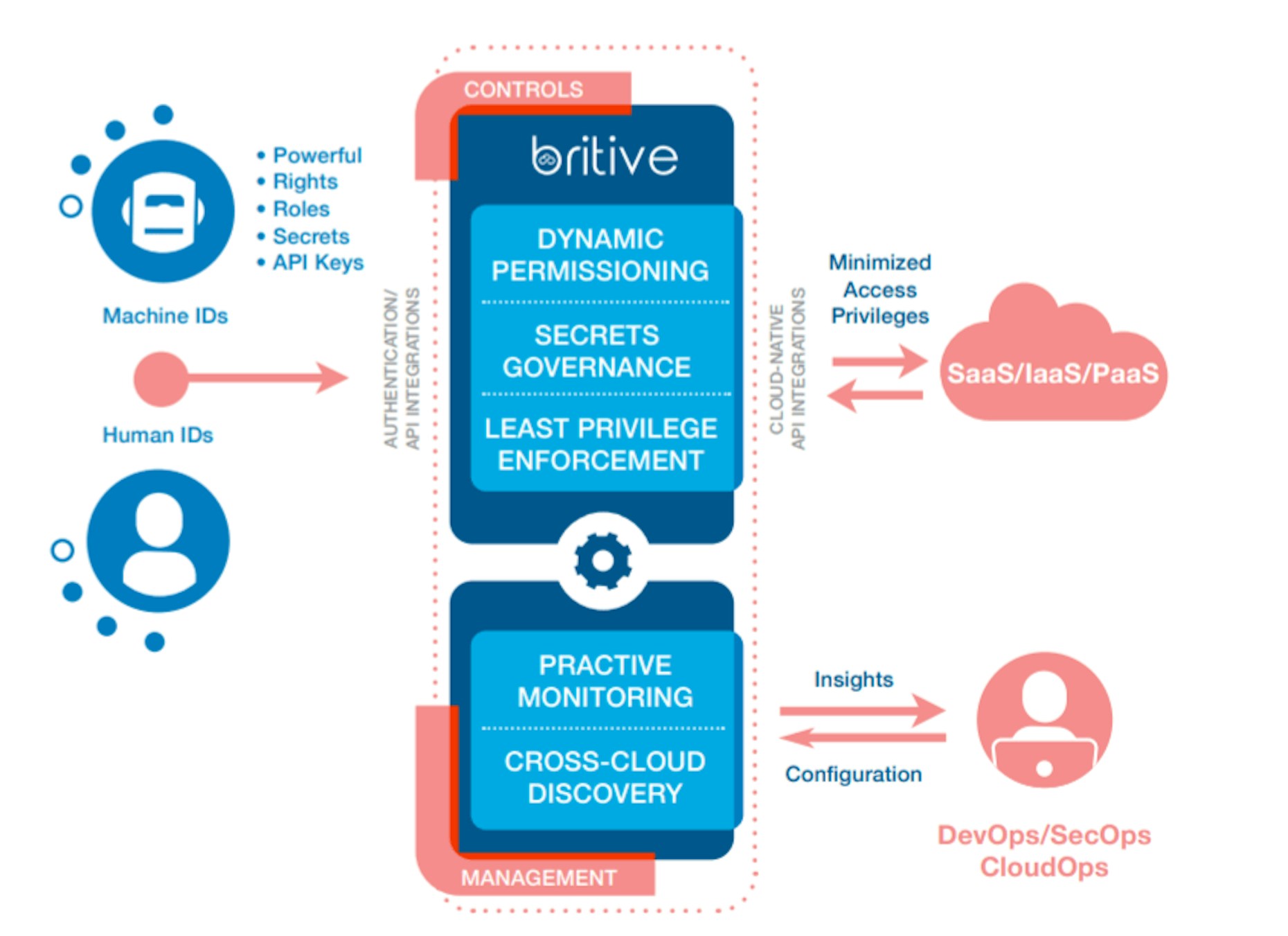
The Britive platform is highly valued by the DevSecOps community for its revolutionary Dynamic Permissioning model. Britive empowers users and machine IDs to grant themselves pre-authorized privileges Just-In-Time (JIT), returning to a state of Zero Standing Privileges (ZSP) once the admin task is completed to minimize the potential attack surface. ZSP enforces the principle of least privilege by ensuring that privileged access is active for users and machine IDs only for as long as needed, for the minimum access level needed, before closing. This type of dynamic permissioning addresses important questions like ‘is this the right amount of access?’ and ‘are those privileged activities appropriate for this role?’”
These capabilities are also highly complementary to other cloud security offerings, especially solutions focused on visibility and analysis for cloud and container workloads such as Lacework. Lacework has built a reputation as a top provider of workload and account security for multicloud and container environments. With the DevOps approach to software and business service development, the proper configuration and compliant use of IaaS services becomes a critical IT security imperatives. By delivering clear visibility in application configurations in AWS, Azure and GCP, Lacework makes it possible for an organization to effectively accelerate and secure its journey to the cloud.
Security at DevOps Speed
The public cloud enables enterprises to automatically scale workloads, deploy faster, and build freely. These attributes support the speed and scale needs of DevOps teams, but they have also has made it increasingly difficult to make sense of the activity happening within their environments. Lacework’s lightweight agent provides visibility to all processes and applications within an organization’s cloud and container environments. The breadth and depth of visibility helps detect vulnerabilities, which can then be addressed and mitigated using Lacework’s machine learning analysis to identify anomalous behavior that poses threats. In particular, the Lacework solution is ideal for:
- Uncovering vulnerabilities in identity and access management (IAM) process.
- Monitoring critical account activities.
- Confirming the security of network configurations.
- Monitoring changes to users, roles, or access policies
- Maintaining visibility into all processes and applications within an organization’s cloud workloads and container environments.
Bolstering and Adding to the Lacework Solution Set
Where Britive can complement the native capabilities of the Lacework solution, and enhance security for its users, is in containing privilege attack surface sprawl and proactively preventing access privilege drift. Crucially, the Britive and Lacework solutions work in concert to secure the entire cloud app development process itself—Britive securing access, Lacework securing configuration and usage—without slowing down or impeding the core business objective of the DevOps-oriented CI CD process: product delivery. The combined solutions work together especially well in the kinds of multi-cloud environments where DevOps projects are increasingly taking place, and which DevSecOps professionals are being asked to secure.
Consider: a typical DevOps operation can easily generate thousands of data access events every day. The result is that each human and machine user ends up having multiple identities and standing privilege sets sitting vulnerable to exploitation—possibly for weeks or months. In an on-premises data center environment, the data and computer resources protected by those privileges would be secured using firewalls and ringfencing, methodologies not effective in the cloud. Britive’s dynamic privileging platform offers a highly effective solution to this problem.
By employing Just In Time (JIT ) privilege grants, users and machine IDs can quickly check out a role-based elevated privilege profile for a specific cloud service, either for the duration of a session or task, for a set amount of time, or until the user checks the profile back in manually. Once the task is complete, those elevated privileges are automatically revoked—all without sys-admin involvement. Where a user previously had standing access privileges potentially extending around the clock for months at a time, converting to Just In time (JIT) granting compresses that attack surface to, perhaps, several hours per week.
Least Privilege Access Enforcement
The concept of least privilege access—permitting the minimal level of access a person needs to do a specific job—is foundational to IT security and for reducing the risk of bad actors gaining access to sensitive data or systems. Lacework’s chief product officer published an excellent blog post on how DevSecOps teams can employ least privilege in AWS to better secure projects in that environment. The Britive platform features several capabilities that empower DevSecOps teams to enforce least privileged access to reduce or eliminate over-privileged accounts as a threat vector, and minimize your attack surface.
Specifically, the Britive platform empowers your DevSecOps team to quickly survey assigned privileges across multiple clouds in order to identify “blind spots” such as over-privileged users and machine identities. With insight like this across clouds, it becomes possible—with security oversight—to remove privileges where they’re not needed and right size privileged access overall. These capabilities are also highly effective for proactively eliminating “privilege drift.” Over time, both standing and dynamic privileges can evolve as roles and responsibilities change—resulting in over-privileged users. Organizations need to be able to automatically monitor and adjust privileges to ensure users have only the privileges needed to do their jobs.
Taken together, the combined capabilities of the Lacework and Britive solutions enable DevSecOps teams to more effectively execute on multiple security and business objectives. Deployed in concert, it becomes possible to secure core CI CD processes without adding new security management overhead—essentially, you can accelerate the cloud app development processes while reducing security risks Britive also fully automate the provisioning and management of privileged account access for DevSecOps developers. Centralized provisioning automates this process across all cloud resources, dramatically reducing the likelihood of errors that can place accounts and data at greater risk.
Read more in our downloadable whitepaper: Six Best Practices for Managing and Securing Cloud Privileges.

