


Dynamic Zero Trust Identity Security for Privileged Access
No Standing Privileges. No Static Access Risk.
Britive enforces Zero Trust across cloud, SaaS, and hybrid environments—without the need for vaults or proxies.
Request a demo
As identity-based attacks surge and insider threats persist, simply managing passwords isn’t enough. Organizations need to continuously verify who is accessing critical systems and limit what they can do, every single time.
The Push for Zero Trust
Identities and the Security Perimeter
Identities and their associated privileges are the new perimeter for security. Standard and privileged accounts with static, always-on access represent a growing attack surface. From engineers to bots to AI agents, access decisions now define exposure. Without strong, identity-first controls, enterprises are flying blind.
Static Access Doesn’t Belong in a Dynamic World
In modern environments, infrastructure spins up and down in minutes. But access entitlements often linger for months, or indefinitely. Legacy PAM tools weren’t built for this level of elasticity. As a result, most environments are littered with unused, over-privileged accounts that quietly expand the attack surface.
Standing Privileges Are Breach Accelerants
A leaked credential tied to a standing admin account is a loaded weapon. Attackers exploit these static permissions to move laterally, escalate privileges, and reach sensitive systems.
Legacy PAM Tools Let Modern Teams Down
Vaults, jump boxes, and manual approvals slow everyone down—and still don’t eliminate standing access. Traditional PAM introduces friction without solving the root problem. Inflexible architectures and hidden costs make them hard to scale and painful to maintain in fast-moving, multi-cloud environments.

Modern Zero Trust Identity Security
Zero Trust Starts with Identity
Modern attackers target credentials, not firewalls. Securing access means verifying who is requesting access AND why every time it's needed.
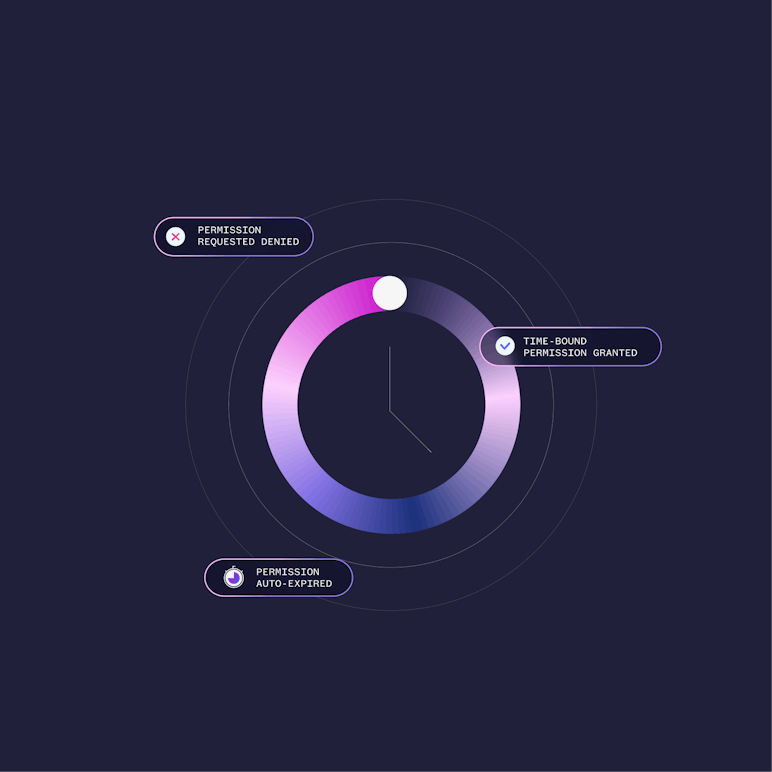
Least Privilege Needs to Be Time-Bound
It’s not enough to assign limited roles. Those permissions associated with roles must also expire. True least privilege means access is scoped and short-lived, reducing exposure from dormant rights.
Access Decisions Must Be Context-Aware
Just-in-time access must consider real-time signals like device posture, location, and role. Static policies can’t adapt to dynamic risk.
Visibility and Accountability Are Non-Negotiable
Get visibility into access for every identity across your entire environment. Security and compliance teams need full audit trails of who had access, what they did, and when.
Britive’s Unique Approach to Zero Trust Identity Security
Britive was purpose-built to enforce Zero Trust in dynamic, cloud-native environments without friction, complexity, or blind spots. We eliminate the risk directly at the source, eliminating standing access and simplifying least-privileged access enforcement to give security teams full control over every identity without impacting the work of other teams.
Just-in-Time Access, by Default
Britive grants privileges only when they’re needed and revokes them automatically when the task ends. No standing access, no dormant admin rights, no lingering risk.
Dynamic, Context-Aware Authorization
Access decisions are driven by policy and real-time context: user identity, request time, resource sensitivity, and more. MFA and step-up controls ensure attackers can’t slip through.
Ephemeral Permissions at the Identity Level
We don’t just vault credentials; our patented JIT technology allows us to manage actual permissions on cloud infrastructure. That means access is created and destroyed at runtime, leaving no static backdoors behind.
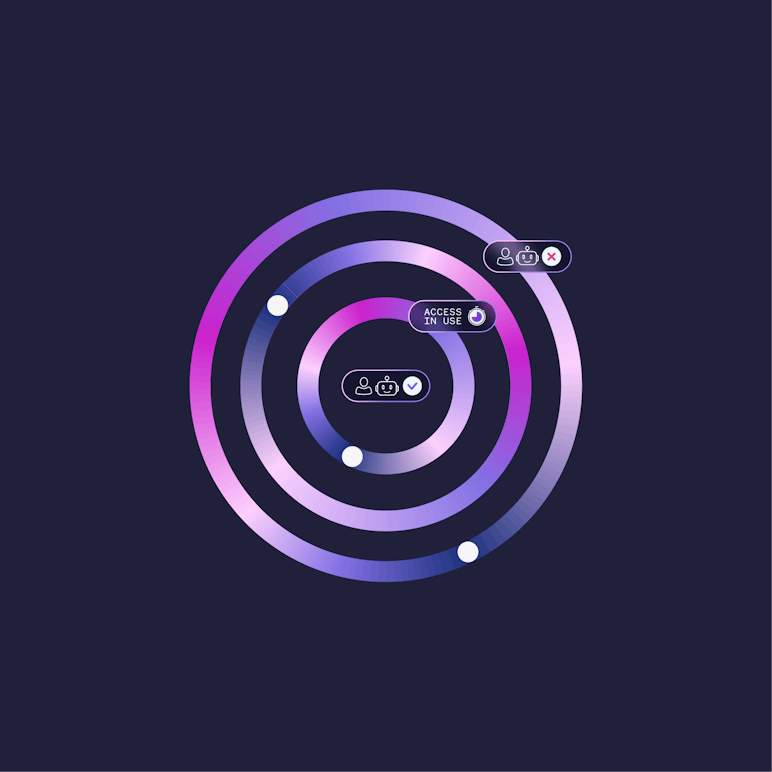
Unified Control for All Identities
Britive governs access for humans, service accounts, automation tools, and AI agents, all from a single policy model. Whether it’s a developer or a bot, least privilege applies.
Built-In Visibility and Auditability
Every access event is logged, linked to an identity, and available in real time. From compliance to incident response, Britive gives you the full picture of who had access, when, and why.
Ready to Deploy. Easy to Scale.
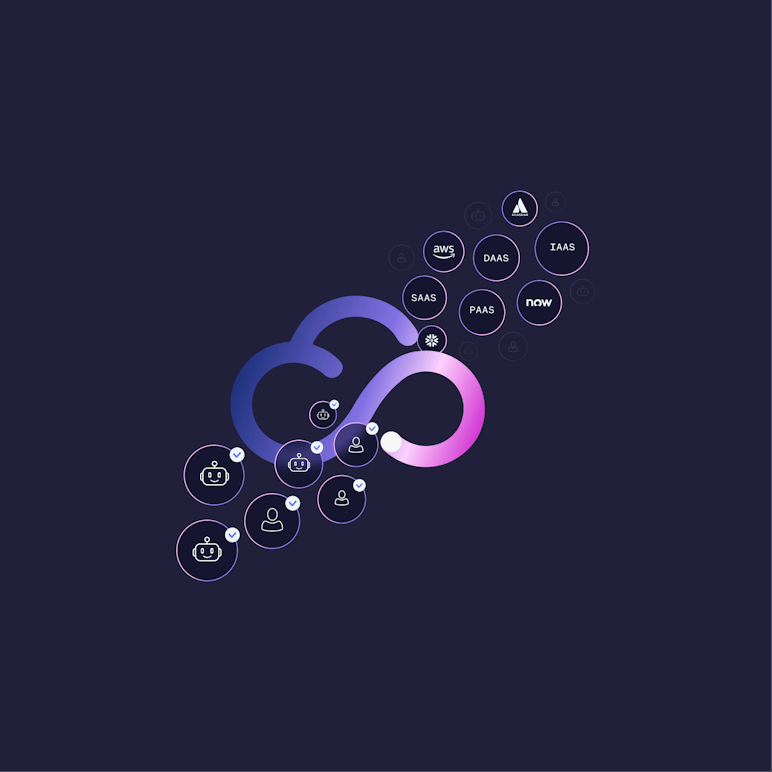
As a SaaS-native, agentless platform, Britive integrates with your identity stack, cloud providers, and DevOps tools—no proxies, no rearchitecting. Most customers are live in days.
REQUEST A DEMOREQUEST A DEMO
Zero Trust Identity Security for Modern Teams
Ready to learn more about how Britive can help you achieve your Zero Trust Identity Security initiatives? Fill out the form to get in touch with one of our cloud security experts.



Case studies
Britive in the Real World
001
002
003
001
002
003



Financial Services Company Streamlines Access Management
Forbes Saves Costs & Removes Standing Privileges to Align with Zero Trust Security
Fortune 500 Retail Giant Eliminates Standing Access Across Growing Cloud Footprint
4000+
54k+
67k+
10,000+
400+
< 30 min
Privileged human identities managed
Static Privileges Eliminated
Static privileges eliminated across all cloud providers
Non-human identities access managed
Identity profiles managed in GCP
Total on and off-boarding time, reduced from 3 days





