
Hard-coded secrets embedded in source code and scattered throughout the DevOps pipeline pose significant risk. Technical professionals responsible for DevSecOps must introduce tools that securely store and manage secrets and enforce access controls without disrupting automated DevOps workflows.
Q: What Problem Does Britive Cloud Secrets Manager Solve?
A: Secrets sprawl.
Secrets Sprawl /see-krits sprawl/ noun
The result of your organization storing secrets (passwords, credentials, API and encryption keys, etc) in a variety of different locations.
Introduction
An organization can use a secrets manager to store sensitive credentials securely. But as the organization grows, secrets proliferate, and it becomes a challenge to manage them effectively.
As a result, cloud organizations need a secrets manager that provides vault security – as well as centralized visibility and control across SaaS and other cloud environments.
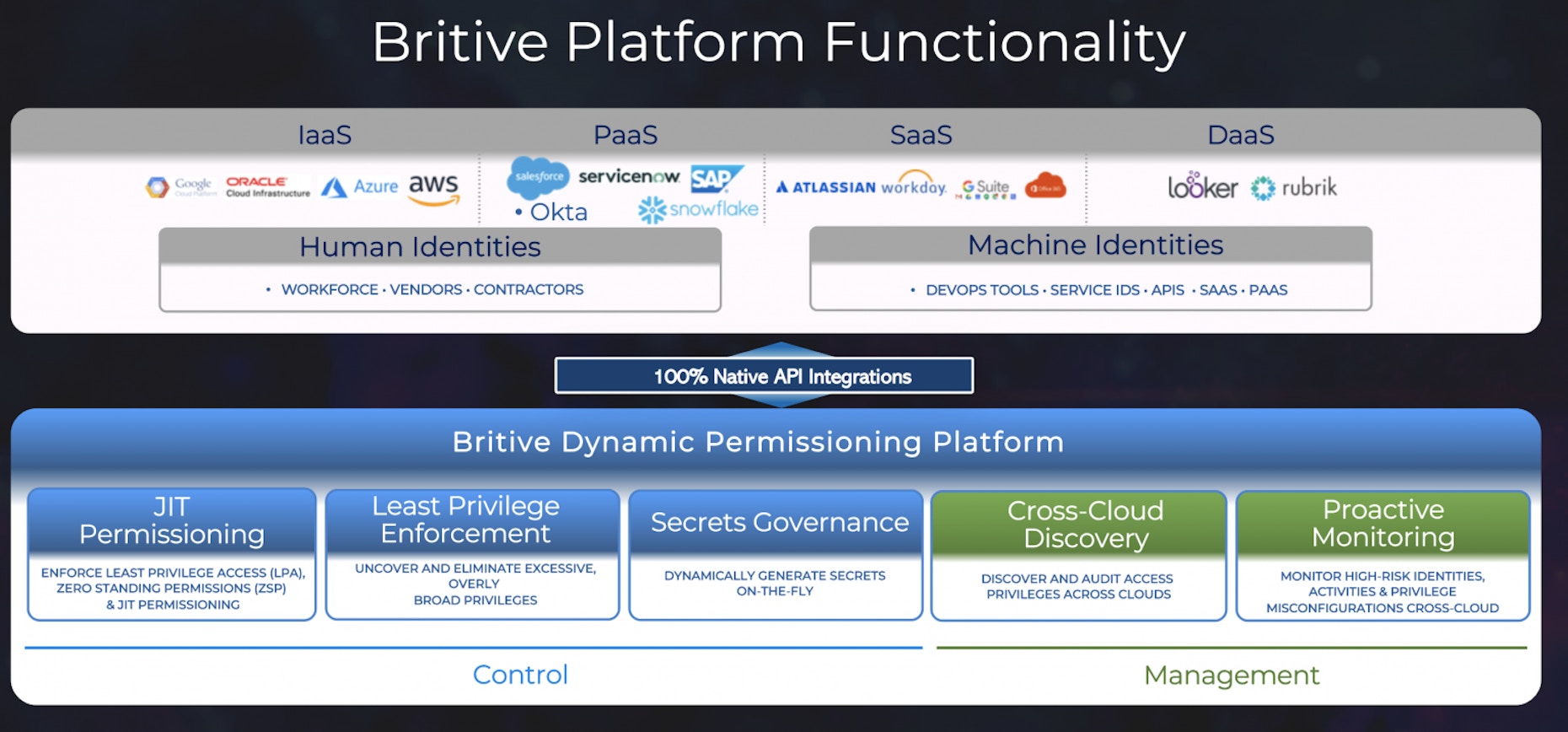
Britive cloud secrets manager is an exciting new component of our dynamic permissioning platform. The manager enhances our SaaS offering by providing the capability to manage secrets and sensitive information accessible by users, APIs, and machine identities.
Defining Secrets in the Cloud
A “secret” in computing is a piece of information that is used to authenticate and authorize an identity so it can gain access to a network, database, or other digital environment.
A secret can be a username or password, database credential, API token, TLS certificate, SSH key, etc.
Both human users and service IDs rely on secrets for access.
Since enterprises have thousands of users across cloud apps and environments, there is a superabundance of secrets to manage and protect.
Companies use secrets managers to manage sprawl.
What does a Secrets Manager do?
A secrets manager helps organizations contain secrets sprawl by centralizing where and how secrets are managed.
Secrets in managers are often rotated – meaning the secret is periodically updated – or dynamic.
On-prem secrets managers and cloud secrets managers, which share similar principles, are different.
Whereas an enterprise’s on-prem environment sits behind a network perimeter, its cloud environment has no perimeter and instead uses identities to authorize and authenticate access.
Therefore, a secrets manager that is designed for the cloud should function within an access platform that can generate and authorize just-in-time (JIT) secrets for each identity that is associated with specific privileges.
The Challenge
Enterprises leverage human and machine IDs to complete DevOps processes as quickly as possible.
That means users often have hard-coded privilege credentials to access sensitive resources. Hard coded secrets ensure builders have the access they need when they need it.
- CI/CD processes depend on instant access to develop applications at speeds that meet business objectives
- Automation allows IT management software to track deployment and usage of technology
- Application servers automate procedures by directly accessing the needed objects and functionalities
The ability to execute processes rapidly drives value and enables companies to scale. However, cyber criminals target automated processes to access privileges and breach cloud environments.
The first challenge organizations face is how to grant and revoke privileges to non-human identities so cloud security does not impede automation.
The second challenge is how to gain and maintain cross-cloud visibility for all identities across the organization.
The Problem with Traditional Secrets Managers
Organizations using open-source or legacy solutions face disadvantages:
- The solution has limited, open-source feature sets or lacks mature cloud capabilities
- The solution is complicated to use and impedes cloud app development
- The solution is costly to buy and deploy (TCO)
Because traditional vaulting solutions lack critical identity and access management (IAM) functionalities, there is an urgent need to elevate secrets vaulting in cloud environments.
Organizations should consider elevating secrets management with a cloud-native, holistic management platform that provides visibility and access for human and non-human identities across all cloud apps and environments.
Cloud Secrets Manager for Enterprise Teams
Enterprises can overcome these challenges efficiently by implementing just-in-time (JIT) secrets.
- Security teams can use JIT secrets to defend against cyberattacks by consistently monitoring machine IDs
- JIT secrets grant and revoke automatically, which significantly reduces the complexity and strain typically carried by Operations teams
- Mission critical applications run as needed so companies can scale
- DevOps benefit from a cloud-native API, which bolsters velocity and simplifies and secures how applications access an organization’s resources
- Compliance and audit teams leverage a Unified Access Model to gain cross-cloud visibility and meet compliance and regulatory requirements
Key questions to ask about your secrets vault
- Does your vault need to provide cross vault visibility into static secrets?
- Does your vault need to integrate with IGA – e.g. SailPoint?
- Does your vault need to integrate with RBAC / PBAC / ABAC?
- Does your vault need to integrate with CI/CD – e.g. Terraform?
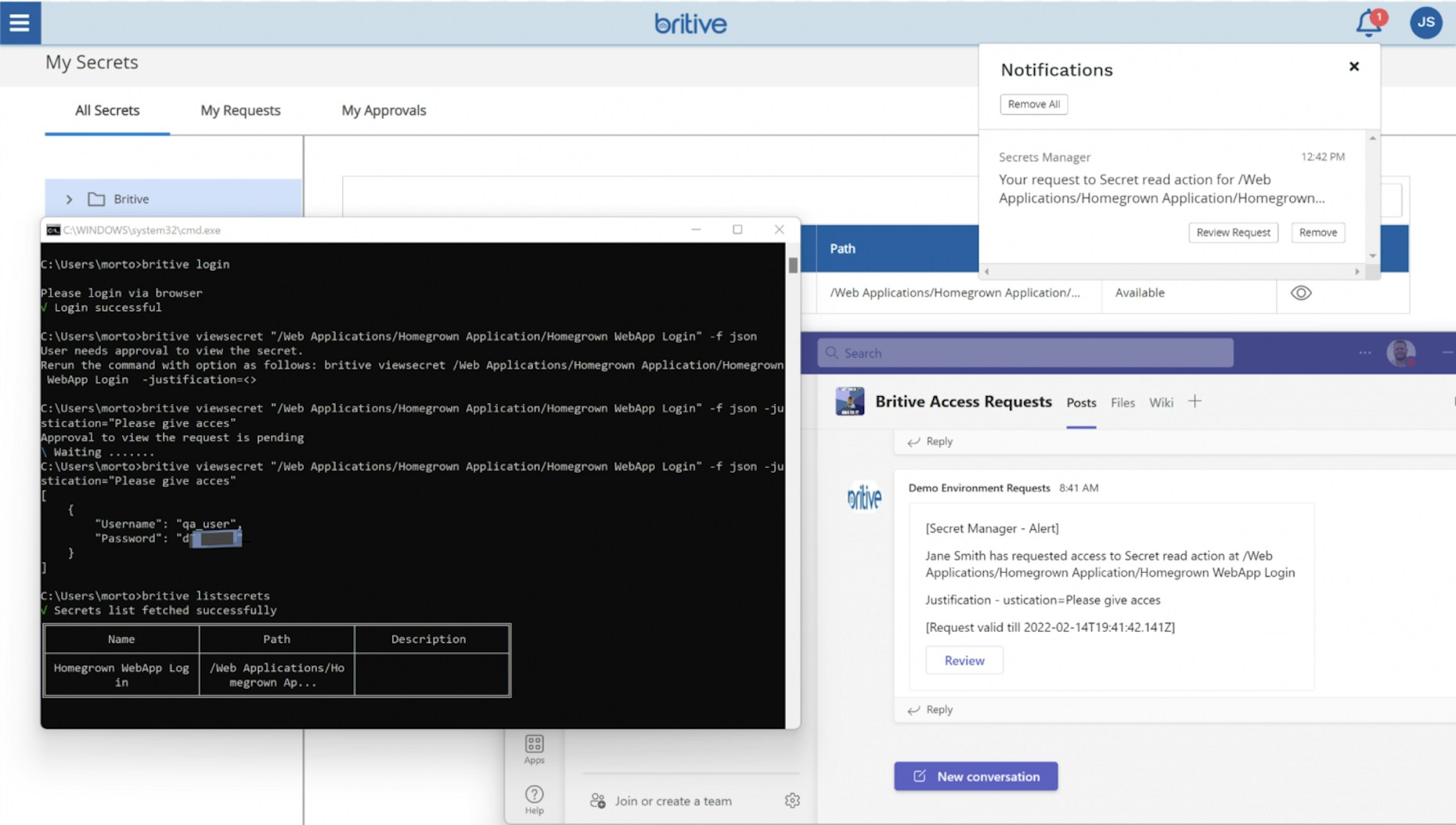
Britive Cloud Secrets Manager
Britive Secrets Manager enhances our dynamic permissioning SaaS offering by providing the capability to manage secrets and sensitive information accessible by users, APIs, and machine identities.
- User credentials
- API Keys
- Notes (free text secrets)
This allows customers to manage privilege escalation, generation of ephemeral credentials, and secrets management in a single-platform.
Enterprise-ready, easy to deploy, and simple to manage, our secrets manager provides the security integrity your organization needs to meet business objectives and scale.
Q: What problem does Britive solve?
A: Secrets sprawl.
Q: What is Britive Secrets Vault?
A: Premier storage for cloud secrets
Britive manages secrets and sensitive information accessible by users, APIs, and service identities.
Q: How Does Britive Solve the Problem?
A: Manages secrets access, generates policy-controlled time-based credentials, and delivers secrets management in a single platform.
- Controls secrets sprawl from a central location
- Replaces embedded API keys in code by retrieving keys on-demand
- Provides visibility into who has access to which secrets
Powerful Business Benefits
- Enable faster adoption of cloud and SaaS
- Accelerate cloud app development
- Remove burdensome security tools that can slow cloud app development
- Reduce infrastructure cost
- Facilitate internal compliance audits
- Quicken time to value and easy deployment
- Simple integration
- Greater ease of use
Empower DevOps Teams
- Reduce your "always-on" risk of credential exposure for machine identities
- Eliminate embedded API keys and static secrets and replace them with ephemeral secrets
- Grant ephemeral API keys to spin up temporary services for testing
- Gain cross vault visibility into static secrets
Core Secrets Manager Functionality
Available February 2022
- Static secrets
- Policy based governance model for access to secrets
- Approval workflows
- Policy-as-code frameworks
- Offline secrets rotation through notifications
- Command-line Access (CLI) to the vault via the Britive CLI
- Comprehensive APIs to access and manage secrets
- Complete auditability for secrets access
- Integration with SSO providers
Want to learn more about the Britive Cloud Secrets Manager?




