One of the most fundamental challenges of securing the identity defined perimeter is the ability to easily manage and secure the cloud identity lifecycle – from the quick onboarding of new employees and contractors, through the maintenance of Least Privilege Access (LPA) and Zero Standing Privileges (ZSP) for those users while they are working in the cloud, to the complete removal of accounts and access when terminated employees and contractors leave the organization.
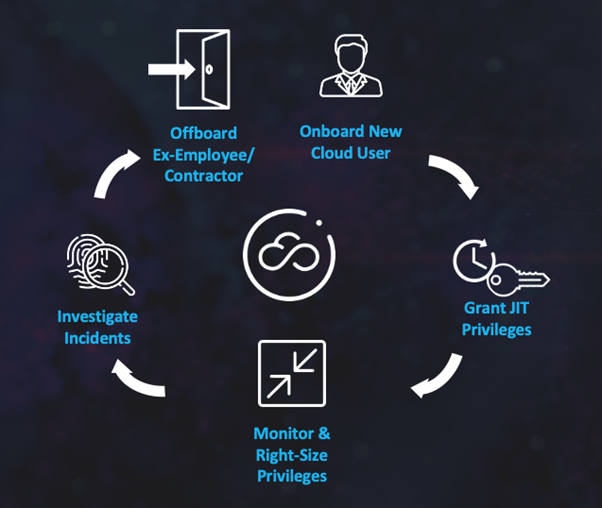
The onboarding and offboarding steps are especially critical in today’s dynamic work environment, with employees and contractors frequently joining and leaving your organization. By integrating the Britive Dynamic Permissioning Platform with your organization’s existing Identity Governance and Administration (IGA) investment, however, your Identity and Access Management (IAM) team can quickly and easily grant role based dynamic access to new DevOps users, manage their permissions while they are working for your organization, and quickly and completely offboard them when they leave.
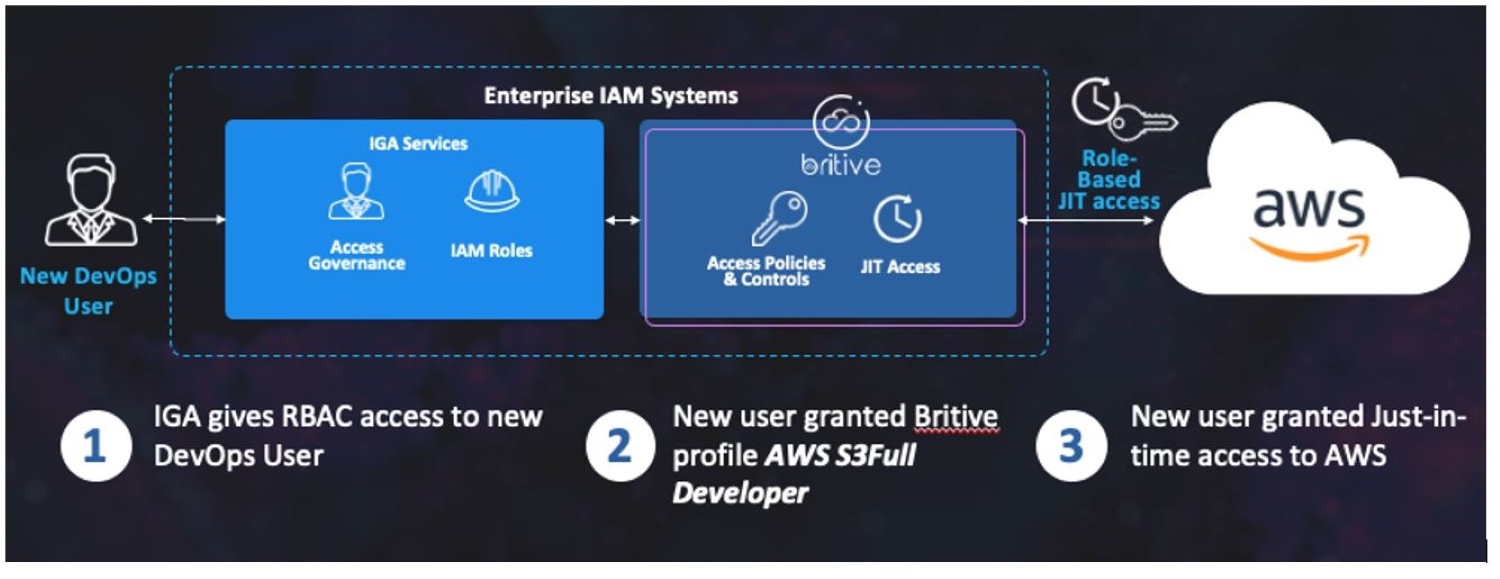
Onboarding a New User with A Just-in-Time Access Profile
Once enrolled in your IGA system, a new user is granted Role Based Access (RBAC), including an on-prem network ID, email, etc. with approval flows for an on-premises admin account. The new user’s group identity is then used to grant usage rights to associated Britive cloud access profiles through API integration of the two systems.
In the example above, a new DevOps user receives access to the AWS S3Full Developer profile, which allows dynamic privileged access to AWS. This profile is made available to the new user to check-out on a JIT ( Just In Time) basis, that is, the permissions contained as part of the access profile are provisioned to the end system only when the user checks-out the access profile.
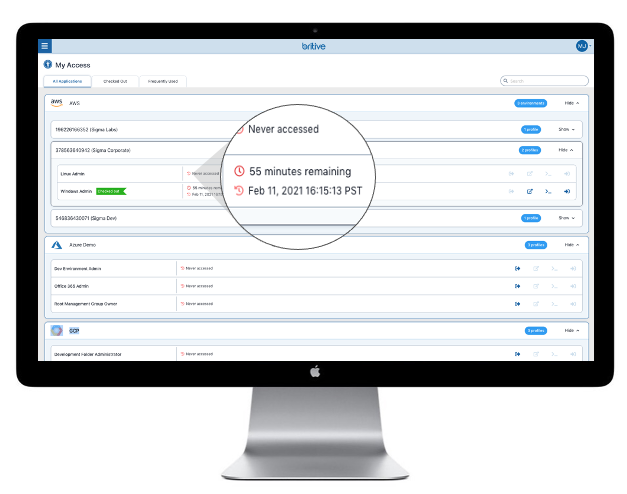
The Onboarded User Experience
Dynamic access to cloud services by end users once onboarded is easy and transparent Upon logging into the Britive Platform, the user is authenticated through the SSO/MFA of your designated identity provider. Once in, they are immediately met with the “My Access” screen”, where they can select from among the profiles available, based on their group identity.
Upon selecting the usage profile, the user can then click a button to check-out the profile and initiate the session for the duration specified in the profile. The session is automatically terminated once the time expires or the user checks-in the profile in accordance with the Zero Standing Privilege (ZSP) model.
Offboarding Users Upon Termination
When an employee or contractor inevitably leaves your organization, it is critical to offboard them quickly and ensure that all access to operation critical cloud services such as AWS have been terminated. This includes expiring API keys, tokens, and secrets that are stored in frequented cloud repositories, I.e., command line credential files stored locally on desktops.
Through the Britive IGA integration, removing a user from their RBAC group automatically terminated their access to the Britive access profiled, effectively revoking their access to the associated cloud services.

