


Back to resources
Securing Cloud Data Platforms in the Age of AI and Token-Based Breaches
October 2025 / 10 min. read /
Recent incidents across major cloud environments have exposed how threat attackers and even automated systems are exploiting identity gaps to reach sensitive data. The Snowflake breach began with compromised contractor credentials that granted direct access to customer data. Cloudflare experienced an internal compromise tied to token and service account misuse following an Okta incident, exposing internal systems such as Jira and Bitbucket. And in a separate event, an AI agent on the Replit platform mistakenly deleted production databases, proving that not all identity risks are malicious, but all can be devastating.
These incidents reveal a common weakness: once access is granted, it often remains active too long, with too much privilege and too little context. Traditional identity systems excel at authenticating who someone is, but not at governing what they can do, for how long, or under what conditions.
Why Data Systems Are the New Critical Control Point for Security
Enterprises today centralize massive volumes of sensitive data across data warehouses and lakes such as Snowflake and Cloudera, cloud storage systems including S3 and DynamoDB, AI and analytics platforms such as Databricks, enterprise applications including SAP and Salesforce, and database platforms such as MongoDB and SQL
This consolidation accelerates analytics and AI but also concentrates on risk. It's no longer just humans, but Agents, pipelines, and ETL jobs now access enormous datasets through non-human identities. If a single key or token is compromised, entire data pipelines, AI models, or production databases can be exposed.
Protecting just the authentication layer alone is no longer enough. Data systems have become critical control point where identity, access, and governance must converge.
Britive’s Modern Solution: JIT, Ephemeral, and Policy-Aware Access
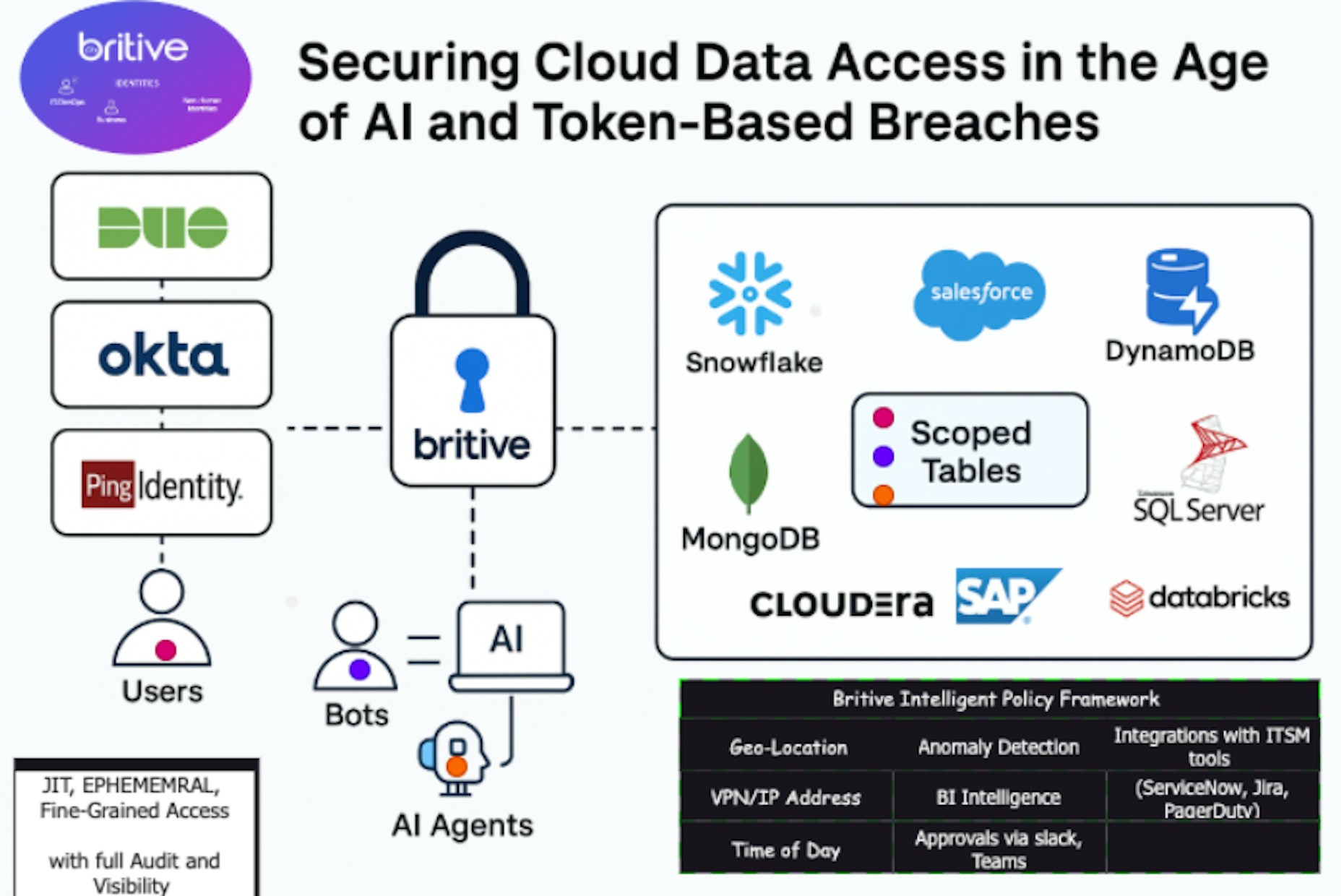
Britive’s cloud-native Privileged Access Management (PAM) and Agentic Identity Security (AIS) capabilities, remove standing privileges and enforces Zero Standing Privileges (ZSP) across the data stack, including Snowflake, Salesforce, S3, MongoDB, SQL, Databricks, SAP, Cloudera and more.
Britive provides Just-In-Time (JIT) access that is temporary and auto-revoked after use, ephemeral credentials that never persist beyond a session, fine-grained control at the schema, table, or API level, and full audit and visibility into every human and non-human access event.
Okta, Duo, Entra, and Ping: Authentication Meets Runtime Authorization
Identity providers like Okta, Cisco Duo, Microsoft Entra ID, and Ping Identity are the foundations of modern authentication. They verify who a user or service is and issue secure tokens using OAuth or OpenID Connect. However, once those tokens are issued, they remain active until expiration and can be reused without additional checks.
Britive complements these providers by extending control beyond authentication into runtime authorization.
Britive adds Just-In-Time access that replaces long-lived roles, conditional controls based on geo, VPN, device posture, and time of day, real-time access approvals through Slack or Microsoft Teams, workflow integration with ServiceNow, Jira, and PagerDuty, and continuous anomaly and behavioral analysis during active sessions.
In simple terms, Okta, Duo, Entra, and Ping authenticate identities. Britive governs what those identities can do, for how long, and under what conditions. Together, they form a unified Zero Trust and Zero Standing Privilege architecture that spans authentication and authorization layers.
A Unified Policy Framework: Context and Collaboration
Britive’s adaptive policy engine evaluates risk and context before access is granted. It combines intelligence, automation, and collaboration for a frictionless experience.
Britive evaluates multiple factors in real time, including geo-location to detect unusual or high-risk regions, VPN and device posture to confirm trusted network access, time-of-day and working hours to prevent after-hours elevation, anomaly detection to catch spikes in data access or unusual activity, behavioral intelligence to understand what normal looks like for each identity, collaborative approvals via Slack or Microsoft Teams for real-time validation, and workflow integration with ServiceNow, Jira, and PagerDuty for automated escalation and compliance tracking.
This framework ensures that no user, bot, or AI agent receives access without complete verification of who they are, where they are, and why the access is needed.
Real-World Scenarios and Examples
- Data scientist receive one-hour access to a Snowflake schema for analytics from an approved region during business hours. The access auto-revokes immediately after completion.
- Cloudera administrator performs maintenance on a Hadoop cluster supporting a production data lake. Britive grants Just-In-Time access to HDFS management and CLI operations for a two-hour window, with full audit logging and automatic revocation.
- Databricks engineer launches a model training job that requires temporary access to S3 and Delta tables. Britive dynamically provisions time-bound privileges to the associated workspace, enforcing geo and time-of-day policies, and revokes them when the job finishes.
- Data platform engineer patches a MongoDB Atlas cluster used by AI pipelines. Britive grants JIT administrative access tied to the engineer’s identity, posture, and location, fully logged for compliance and automatically revoked afterward.
- Finance systems analyst requests elevated access to a SAP HANA database to run a quarterly reconciliation job. Britive issues Just-In-Time privileges restricted to that schema and role, requires real-time approval through ServiceNow, and revokes access automatically once the task is complete.
- Site reliability engineer attempts after-hours access to an AWS S3 bucket. Britive’s anomaly detection flags the unusual activity, triggers a Teams approval workflow, and automatically denies access if not validated.
- Developer uses a static AWS access key to query DynamoDB and Redshift for testing. When that key is inadvertently shared or left in a script, it provides ongoing access to sensitive data outside of corporate controls. With Britive, those static keys are replaced with ephemeral, Just-In-Time credentials scoped to a specific user, action, and time window, removing persistent risk and simplifying audit compliance.
Britive enforces least privilege dynamically across every type of data system, from modern cloud warehouses and lakes to enterprise ERP platforms like SAP, bringing together context, collaboration, and visibility to eliminate standing access and prevent data misuse.
AI Pipelines, Agents, and the Britive MCP Gateway
AI and automation workloads rely heavily on non-human identities such as scripts, connectors, and AI agents. Traditional OAuth-based integrations provide authentication but lack contextual and time-bound authorization. Tokens issued to agents or tools can remain valid for long periods, often with overly broad scopes that allow destructive actions to occur unchecked.
Britive’s MCP (Model Context Protocol) Gateway extends runtime access control and context-aware enforcement to AI agents and automated systems. It acts as a policy-aware broker between models, data, and actions, ensuring that AI-driven operations only execute within approved context, permissions, and intent.
For example, in the Replit incident where an AI agent accidentally deleted production databases, Britive’s MCP Gateway can guard against those disruptive actions, by intercepting the delete command, validated its context, and either completely block the agent action with notification alerts or required human approval with step up MFA, before execution. Even if the underlying data system allowed the delete operation, Britive’s MCP Gateway would have blocked it in real time based on model context and policy, ensuring no destructive action could be executed without verification.
This capability provides guardrails that protect both human and machine workflows, ensuring that automated intelligence operates safely, within policy, and with full visibility.
Action Plan for Data Security Teams
- Identify all human and non-human and agentic AI identities that access data.
- Remove static credentials and long-lived tokens.
- Implement Britive JIT access with contextual and collaborative policies.
- Replace static AWS keys with ephemeral, policy-aware credentials.
- Monitor activity in real time with anomaly and behavioral analytics.
- Extend coverage across all data systems including Snowflake, Cloudera, Databricks, SAP, DynamoDB, MongoDB, and S3.
Britive is a well-architected SaaS platform with no infrastructure for customers to manage cloud, SaaS, data systems or Kubernetes environments. A new customer tenant can be deployed in a matter of hours, allowing organizations to immediately strengthen their security posture and reduce significant risk from day one
Final Takeaways
The next generation of breaches will involve human users, non-human identities, and AI-driven agents acting with excessive privilege. MFA, SSO, and OAuth alone cannot prevent this. The future of data security requires runtime access control that adapts dynamically to who or what is requesting access, when, and why.
Britive delivers that control in a SaaS-native, cloud-scale platform that secures data platforms and AI systems at runtime. It integrates seamlessly with Okta, Duo, Entra, Ping, and your collaboration and ITSM tools to unify identity, intelligence, and operations.
See how Britive can help secure your data and AI pipelines today — schedule time for a discussion with a member of the team.


