
Agentic AI and the New Identity Challenge
AI is no longer just answering questions or writing content. It is starting to act, collaborate, and even make decisions on our behalf. And that shift fundamentally redefines everything about how we think about identity security.
Until now, most identity programs focused on human users, employees, partners, and customers. As cloud adoption scaled, organizations also had to manage a fast-growing set of non-human identities (NHIs) such as service accounts, scripts, bots, and automated cloud workloads. These identities are typically static, task-specific, and deterministic in behavior.
Now, Agentic AI introduces a third, distinct identity category. These are autonomous software agents powered by LLMs that can interpret data, reason, collaborate with other agents, and adapt based on outcomes. They interact with APIs, query sensitive data, negotiate decisions, and even initiate actions without human approval. While NHIs are typically passive and scripted, Agentic AI identities behave much more like dynamic, decision-making humans—but at machine speed.
This makes securing Agentic AI different than NHIs—because it requires continuous, intent-aware, and context-sensitive authorization, not just static access control.
If your company is building or using these systems, then every agent is now an identity. And if you are not securing what those identities can see and do, you are opening the door to risks you may not even be aware of.
Real-World Example: AI-Powered Family Vacation Planning
Let’s walk through a use case you can visualize.
Imagine a company like Expedia or Hopper offering a year-round vacation concierge powered by AI. The user does not browse or filter, they simply say:
“We want two or three family vacations this year. Something relaxing, something outdoors, maybe a city trip. The kids are nine and twelve. Budget is twelve thousand dollars.”
Now behind the scenes, a group of intelligent agents picks up the request and goes to work:
- Preference Planner Agent reviews the prompt, analyzes past trips, and splits the budget across seasons and trip themes
- Destination Matchmaker Agent finds top destinations for each trip, based on weather, travel time, kid-friendliness, and seasonal trends
- Deal and Logistics Agent connects to booking APIs, checks visa rules, validates passports, and surfaces the best combinations
- Trip Builder Agent assembles two or three options, uses an LLM to generate summaries with pros and cons, and creates a ready-to-review plan
- Approval Agent sends the itinerary to the parents via email or text with options to approve, revise, or ask a follow-up
These agents are not just bots. They reason, collaborate, and adapt. They connect to systems like PostgreSQL for customer profiles, MongoDB for past travel history, MySQL for product catalogs, and external APIs to get deals and restrictions.
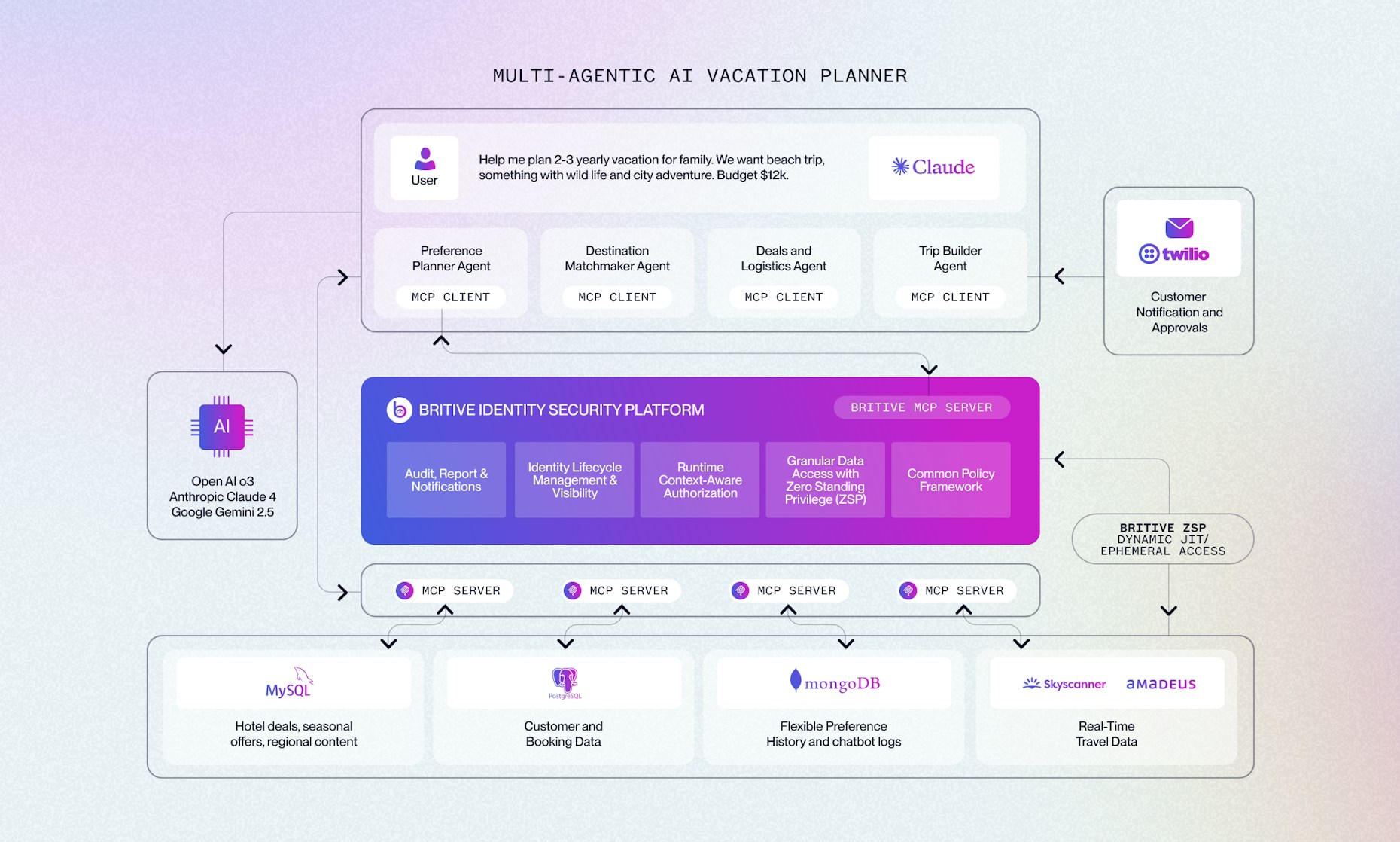
The diagram above shows how agents interact with databases, LLM, Amadeus, Skyscanner, and secure APIs using role-based access through MCP.
How Agentic AI Is Different from Bots and RPA Tools
Let’s pause here for a moment. Some folks reading this might be wondering “wait, isn’t this just automation or RPA with a fancy new name?”
Not even close.
Traditional RPA tools and workflow bots are good at repeatable tasks. They follow predefined rules, operate in silos, and do exactly what you tell them, nothing more, nothing less. That’s useful for things like filling out forms or scraping structured data.
But Agentic AI is a different beast. These are intelligent agents with specific goals. They use LLMs to reason through problems, they talk to each other to share context, and they make decisions on the fly based on changing inputs. And importantly, they know when to ask for help.
Here’s how they differ in practice:
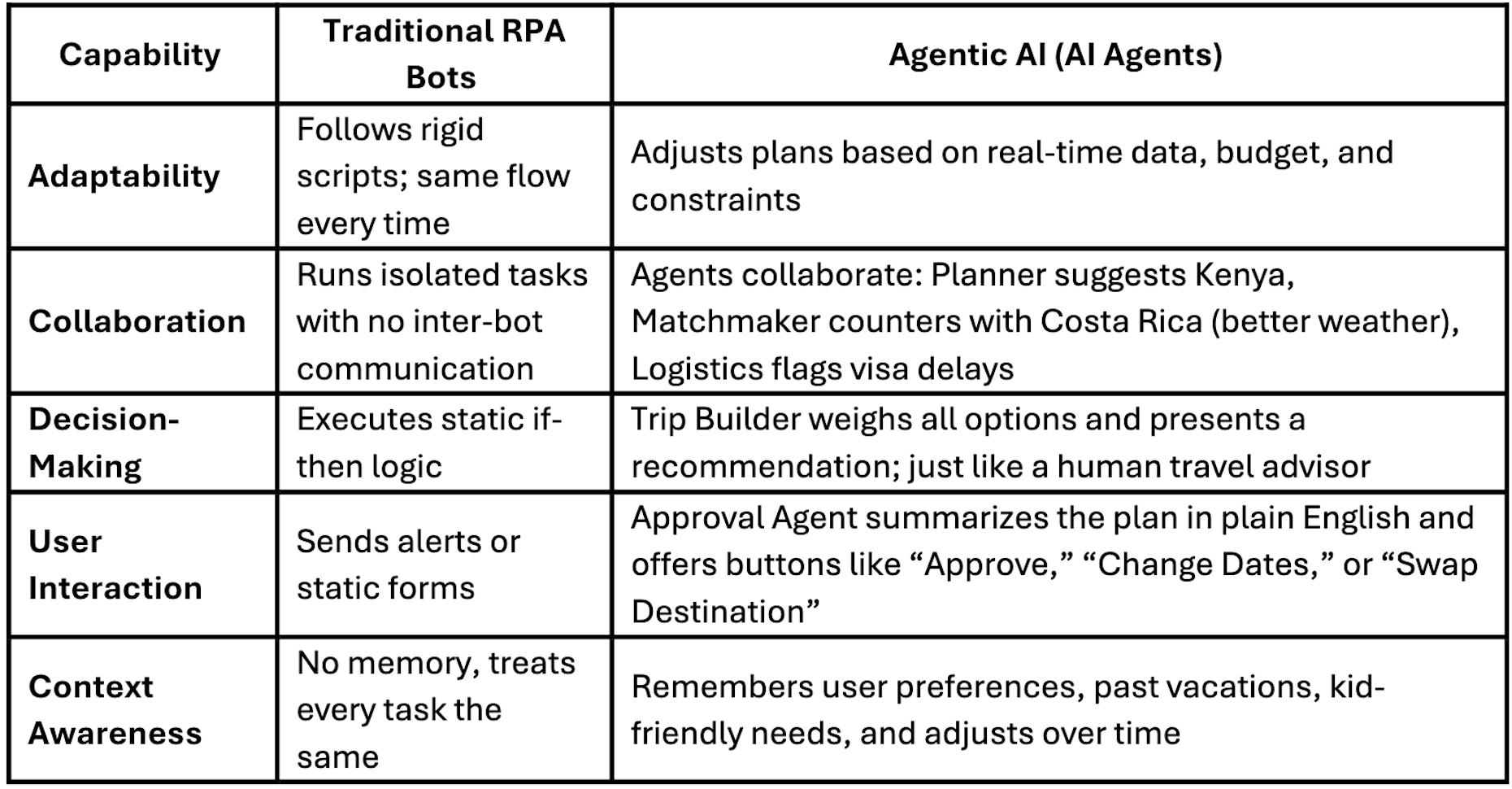
That’s not scripted automation. That’s autonomy, reasoning, and shared decision-making.
And just like with any smart employee, you need to manage what they access.
The Security Risk Beneath the Surface
Now imagine this happening across thousands or millions of users. Agents accessing sensitive customer data, calling external APIs, and triggering transactions.
Without robust, identity-centric security boundaries specifically designed for this autonomy, it becomes a massive, unmanageable risk.
- Agents may retain access to data they no longer need
- They may overreach into payment systems or profiles
- API keys can get embedded in code or logs and get reused
- There is often no granular audit trail showing which agent accessed which system or data, when they did it, and why; leaving no correlation between agent actions and business context.
These are not hypothetical risks. Real-world breaches prove the point.
- The LastPass breach exposed user vault data due to an over-permissioned DevOps identity
- The SolarWinds incident used automation credentials to move laterally and compromise a software supply chain
- Verizon reported that most ransomware attacks involve compromised credentials, often belonging to non-human identities. Agentic-AI is just going to massively accelerate this risk that must be addressed.
This is where the 80-20 rule becomes painfully real. While security teams often focus on edge cases, the reality is that 80 percent of breaches are caused by identity-related issues, including excessive privileges, static credentials, and lack of visibility. And most of that 80 percent starts with a non-human identity like a bot or a service account.
Agentic AI takes that risk and accelerates it. Now identities are not only connected; they are intelligent and autonomous. And unless you’re governing them with precision, you are opening up a breach window at machine speed.
Solving the Problem of Secure, Autonomous AI Access
Britive was purpose-built for exactly this moment, born in the cloud to address these modern identity challenges head-on
It applies a Zero Standing Privilege model across human, Agentic AI, and non-human identities (NHIs). Access is dynamically granted just-in-time, precisely scoped to the task, and automatically revoked immediately after use
This means no static credentials, no standing privileges, and no "always-on" God-mode access, which is the core tenet of true Zero Standing Privileges.
In the AI vacation planner example:
- The Logistics Agent only gets access to booking systems during a valid session
- The Matchmaker Agent is restricted to destination data and cannot access payment systems
- API credentials are injected securely through Britive and expire automatically
- Customer data access is scoped to session and context, so no agent can browse data it doesn’t need
- Every action is logged and mapped to the agent’s identity and task
Britive treats agents the way we treat human users: with precision, policies, and visibility.
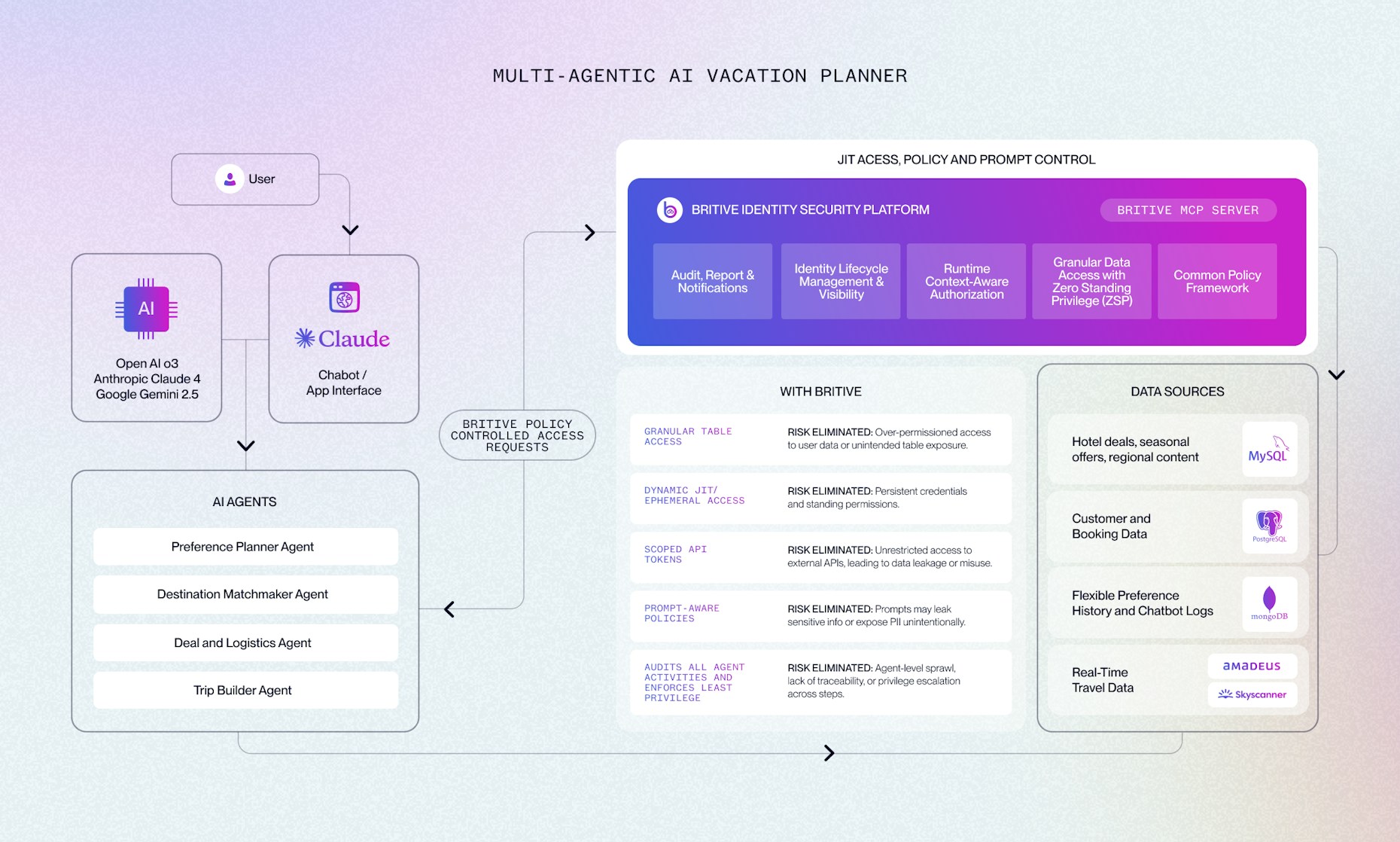
This diagram illustrates how AI agents interact with user prompts, LLMs, and backend data, while Britive enforces security at every step. From customer data access to LLM prompt scoping and API token injection, Britive ensures each agent accesses only what it’s authorized to, for only as long as needed.
The Impact for Business & Security Leaders
This is not just about securing AI. It’s about empowering your organization to innovate confidently, protecting your brand, safeguarding your users, and accelerating your business velocity without sacrificing security or speed.
Britive enables companies to:
- Build intelligent systems faster without creating exposure
- Contain risk by limiting access for every identity, human or agent
- Eliminate manual secrets management and policy sprawl
- Provide audit and compliance teams with full visibility across cloud, SaaS, and on-prem
- Stay ahead of the AI curve with controls that move as fast as your architecture
When security aligns with the flow of how things actually get built and shipped, it becomes an enabler. That’s what Britive does.
The Shift Is Already Underway, and the Market Knows It
This isn’t just a few forward-leaning teams making a bet on modern access. The entire industry is moving.
Gartner predicts that by 2026, 70 percent of organizations will adopt just-in-time privileged access as a foundational strategy to reduce standing privileges across cloud and DevOps.
But here’s the important part. JIT isn’t new. What’s changing is how it gets done.
In the legacy world, JIT still relies on old constructs like vaults, credential checkouts, agent- and proxy-based architectures, and broad access policies. You request access, get a long-lived credential or broad role, and are left hoping the static policy is correctly scoped and the credential isn't later misused. That’s not zero trust, and it’s definitely not zero standing privileges.
Modern enterprises can’t afford to operate that way anymore. The systems are faster, the architecture is ephemeral, and the identities now include LLM-powered agents making real-time decisions. This isn’t a use case you can solve with more vaulting.
Aragon Research recently released a research note defining a new category in the market: Agentic Identity and Security Platforms, detailing key platform capabilities to handle the complex requirements of these new identity types.
This is where the principles of Zero Trust and ZSP come in.
What Zero Standing Privilege Looks Like in Practice
- Access is ephemeral and scoped only to the action or task, not based on broad, static roles.
- There are no passwords to check out or rotate.
- Secrets are injected on demand and never stored.
- Every identity, human, machine, or AI Agent, is governed policies through a single, unified platform.
- Access is logged, auditable, and aligned to task context.
Security doesn’t slow things down. Instead, it becomes the reason your AI systems, DevOps teams, and internal auditors can all move more efficiently, and with confidence.
Modern Leaders Are Already Making the Move
At Britive, we’re seeing a growing number of security leaders quietly shift away from legacy PAM thinking. They’re not making headlines for it, they’re just getting it done.
They’re choosing tools that integrate seamlessly with cloud platforms. They’re aligning identity strategy with how their engineering teams actually work. They’re securing AI agents and non-human identities with the same discipline they apply to admins. And they’re building with just-in-time, zero standing access from the start.
These are the same leaders who aren’t waiting for the next breach report to validate their decision. They’re looking ahead, they’re staying lean, and they’re building security that fits the future.
Final Thoughts
If you’re a CISO or infrastructure security leader still evaluating the options, this isn’t about fear or pressure, it’s about clarity.
The question isn’t whether identity is a risk, it’s whether you’re solving the right part of it.
The boldest security teams aren’t just replacing tools, they’re rewriting assumptions. They’re leaving behind vaults, static credentials, and slow processes, and they’re choosing access that moves with the workload, with the user, with the future. Britive is here to enable those teams.





