


Back to resources
How Zero Standing Privileges Clear the Way for Zero Trust Model
February 2022 / 5 min. read /

There is a reason the security community has embraced the zero trust (ZT) principle with renewed energy – it helps prevent breaches by eliminating implicit trust from a system's architecture.
Instead of automatically trusting users inside a network, ZT dictates that every access point requires validation.
All users, human and non-human, whether they're accessing resources on-prem or in the cloud, must be authenticated, authorized, and validated for security configuration and posture before being granted access to applications and data.
Shifting network defenses toward a comprehensive security model like Zero Trust allows organizations to restrict access controls to networks, applications, and environments. This improves granularity and reinforces an additional layer of security across data.
Rather than trying to protect an ever-evolving attack surface, Zero Trust architecture, and policies fundamentally defend networks through consistent monitoring and maintenance.
As good as zero trust sounds in theory, however, putting it into practice is difficult. The reasons for implementing ZT are clear, and it is wise to do as much as possible toward enforcing ZT policies quickly.
But when an organization has multiple environments with thousands of users that operate on established processes, it's easy to see why they struggle to implement it in its entirety.
The problem is exacerbated in the cloud, where proliferating service IDs and human users work in concert to develop software at a rapid pace to achieve scale.
So how do security teams develop ZT policies that do not impede workflows?
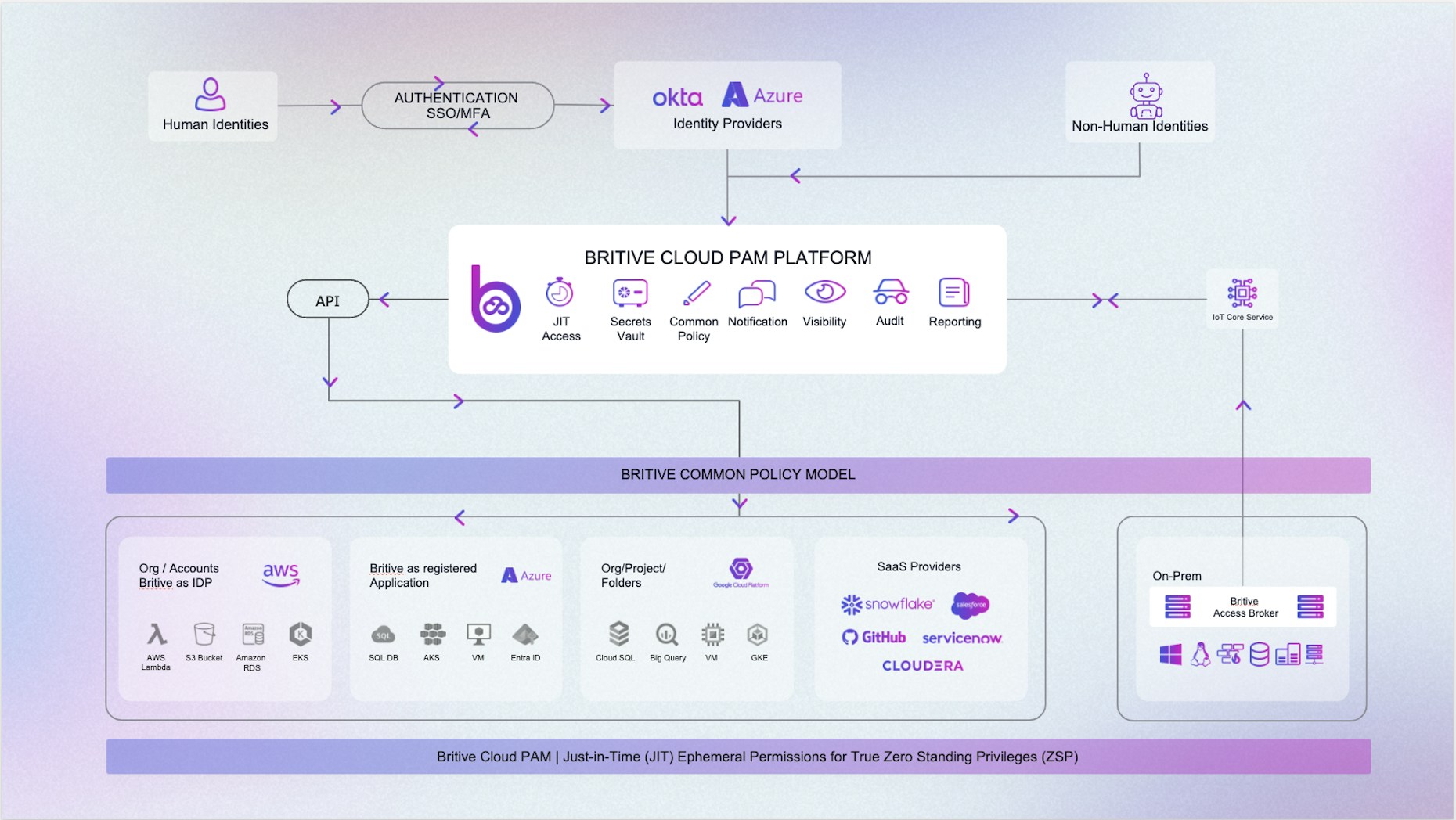
Implementing Zero Standing Privileges to Achieve a Zero Trust Model
Organizations move to the cloud for speed, agility, and cost-savings. And while it is understood that cloud and on-prem environments are fundamentally different with unique security requirements, a common challenge between them is the lack of visibility and control among users and access management. Validating and monitoring every user across each environment would be a Herculean task.
As a result, any organization attempting to implement ZT risks slowing the pace that teams need to maintain to meet business objectives.
The irony is that developer models with a need for speed do not have to be at odds with the security controls recommended by zero trust. The friction arises when you try to fold ZT policies into an existing network architecture designed for velocity.
DevOps cannot be encumbered by strict security controls, and security controls must not impede DevOps’ ability to deliver the goods.
It's the dynamic of fitting a square peg into a round hole that prevents most companies from achieving Zero Trust.
But if Zero Trust policies are implemented through strategic access management practices, DevOps can build quickly and SecOps can protect an organization’s data, applications, and networks.
But without effective Zero Trust, an organization's attack surface continues to grow and user access management becomes increasingly cumbersome and difficult to see.
When a security incident occurs, everything grinds to a halt as time is spent trying to work backward, figure out what happened, and prevent it from happening again.
To solve this riddle, let’s step back from zero trust and focus on zero standing privileges (ZSP).
Zero Standing Privileges
Gartner defines ZSP as “the target state for privileged access in an organization to minimize risk of stolen credentials, privilege abuse, breaches, data loss and non-compliance.”
Unlike Zero Trust, which is a comprehensive security framework that can be interpreted in diverse ways, Zero Standing Privileges is a tactical step and principle that organizations can implement to move closer to a complete Zero Trust model.
Utilizing dynamic JIT permissions is one way to achieve Zero Standing Privileges across your environment, which enables DevOps and security operations teams to achieve their respective objectives.
DevOps have the access they need when they need it. Permissions are granted just-in-time with minimal delay, while Zero Standing Privileges improves the overall security posture by ensuring access exists only when needed.
Organizations of all sizes across industries recognize the importance of moving toward a Zero Trust policy, but it's easy to get sidetracked on the way there.
Zero Standing Permissions is one of the fastest and most assured ways of securing users in cloud environments without slowing down DevOps.
Maintain ZSP across your entire cloud environment with ephemeral Just-In-Time (JIT) privileges. A unified access model provides cross-cloud visibility for human and machine IDs across all operation-critical cloud applications.
Britive's patented JIT technology and Cloud PAM platform:
- Minimizes the blast radius of your highest risk permissions.
- Eliminates standing privileges and over-provisioned accounts.
- Automatically grants & revokes elevated privileges without manual processes and involvement.
- Seamlessly integrates across the entire environment with it's API-first design, reducing unnecessary friction.
Remember, permanent elevated privileges leave you open to increased data loss and account damage due insider threats and hackers 24/7.
Temporarily granting and expiring JIT privileges with Britive instead minimizes the potential blast radius of your privileged human and machine identities – all while making sure DevOps has the access it needs to achieve velocity and grow your business.
Ready for more advice on how to extend Zero Trust across the entire identity lifecycle? Get more insight from our download: Zero Trust in the Cloud Era.

