Back to resources
Watch the Demo: Just-In-Time Access for Snowflake Roles and Databases
April 2022 / 4 min. read /

Just-in-Time Access for Snowflake
We are excited to share that Britive now offers Just-in-Time (JIT) temporary access for Snowflake administrative roles and databases.
Britive delivers the visibility and control you need to secure data access and eliminate standing privileges.
In this blog post, we will explain how JIT access for Snowflake works, and why it plays a critical part in protecting sensitive data across warehouses, data lakes, and other cloud data sources.
Snowflake
Snowflake helps customers gain access to data services, data governance, and use data to drive business forward, which is why it's critical to have visibility and control into which permissions roles can access.
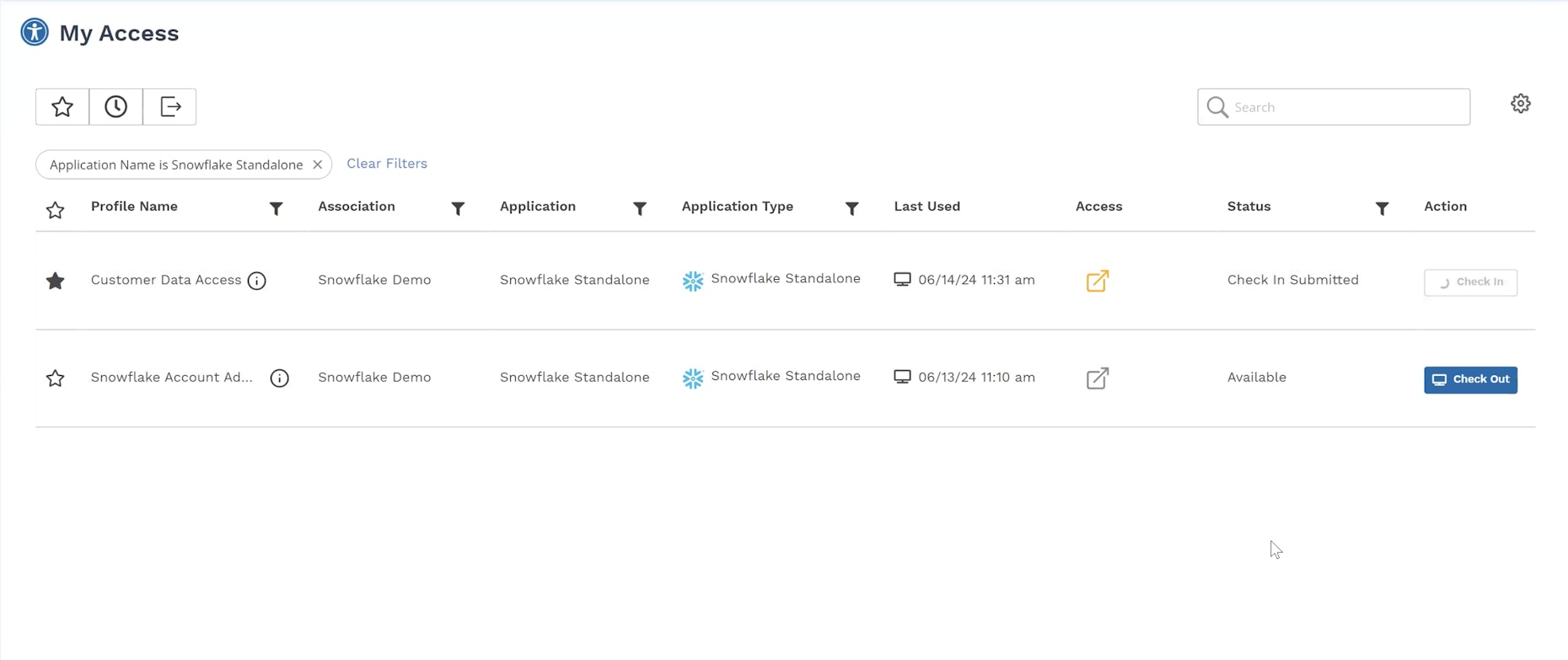
Britive allows you to build Snowflake profiles and dictate access based on security policies. What's more, the temporary, dynamic nature of JIT permissioning means users have access only when they need it, i.e., roles, privileges, and data have permissions associated to them by policy, and administrators can automatically grant and revoke those permissions on-the-fly.
The benefits are immediate: uninterrupted workflows, elevated privileged access management, and greater visibility across data clouds.
Despite the clear advantages, many organizations struggle to implement JIT permissioning in ways that are cohesive, streamlined, and data driven.
Poor Visibility = Weak Enforcement
A primary challenge customers may face when trying to achieve Least Privilege Access (LPA) to their data cloud comes down to visibility and enforcement.
For context, think of it this way: what good is visibility without enforcement? And what good is enforcement without visibility?
- Without visibility it is extremely difficult to role right-size and understand how and when privileges are used
- Over-privileged access leads to standing permissions, which are a serious security threat
- Business priorities demand speed, meaning users need constant access to data––heavy security controls slow down workflows
- Organizations must decide whether to put business priorities or security first
Britive believes cloud organizations should not have to make this choice. We bridge the gap between security and business – JIT permissioning is how we do it.
Programmatic JIT in Snowflake
Britive JIT access seamlessly integrates with programmatic tooling—such as Python, Jupyter Notebook, etc.— used by data scientists and DevOps teams. Programmatic JIT access detaches roles from identities, removes static access, and keeps data lakes secure. Teams can quickly scale up using a single role checkout.
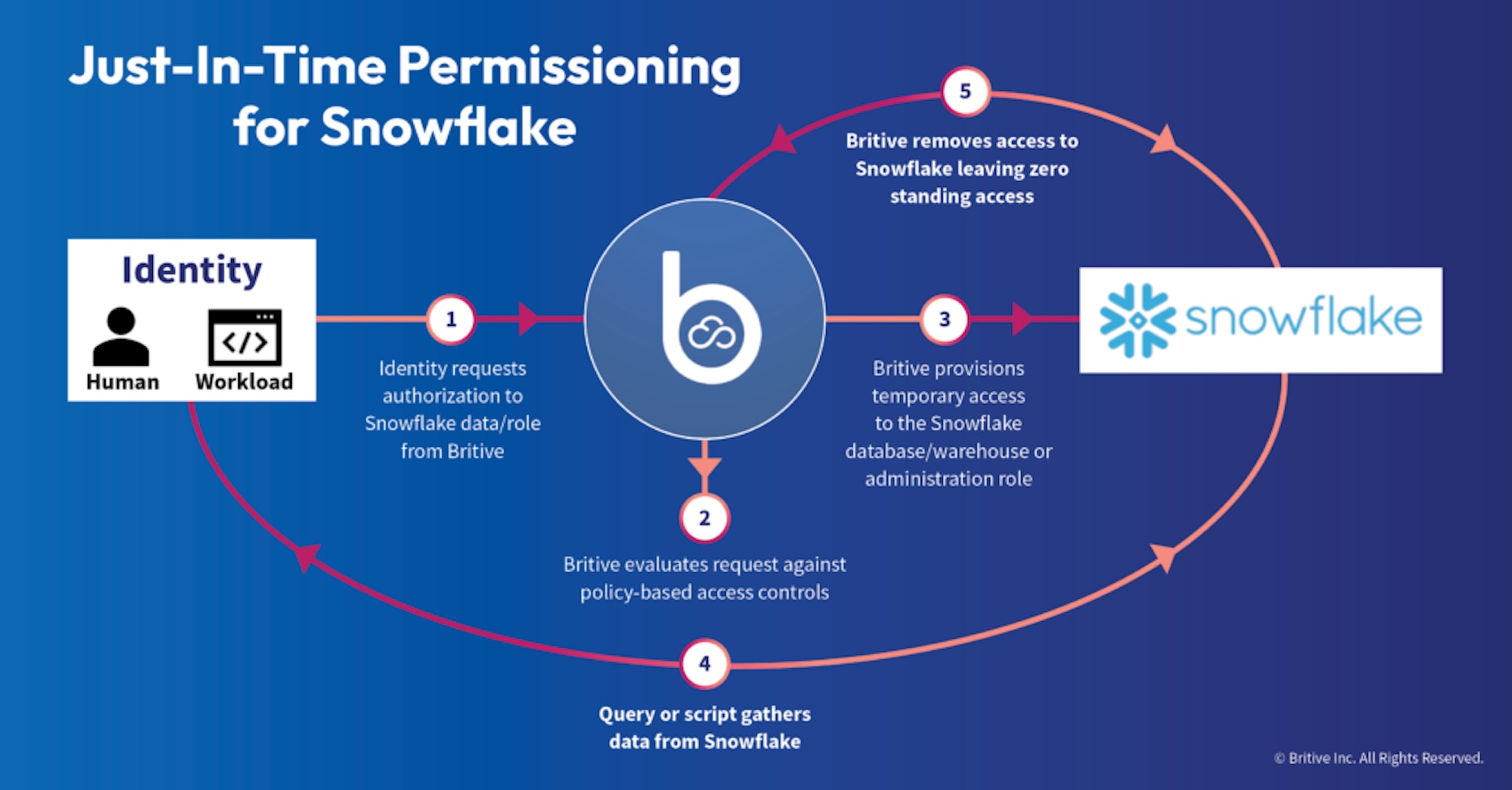
How it works:
Step 1: Create policies that support LPA and Zero Standing Permissions (ZSP)
NIST (National Institute of Standards and Technology), Gartner, CSA (Cloud Security Alliance), and other cloud control security matrixes recommend enforcing least privileged access and zero standing permissions.
A proven and efficient method of achieving LPA and ZSP is via JIT permissioning.
Step 2: Assign privileges to users based on policy
Establishing best practice policies is one thing; enforcing them without impeding workflows is another.
This is where many organizations struggle. As mentioned, it is difficult to enforce policies when visibility is limited.
But when roles are clearly defined, and visibility into users is total, enforcing best practice security policies is attainable. Data is accessible and protected – always.
Step 3: Grant and revoke permissions using JIT
Imagine the peace of mind that comes from knowing that only authorized users can access your data – data scientists can execute successful queries only when access is granted – while standing permissions and/or over-privileged users cease to exist. Just-in-Time access for Snowflake gives you maximum control and ease of use.
Britive lets you establish and manage policies, understand and control data use in Snowflake, and eliminate standing privileges.
Capitalize on Snowflake's powerful data capabilities and support key business drivers through temporary, JIT permissioning.
Watch the Demo
Watch the demo to see JIT for Snowflake in action.