
About the Latest NOBELIUM Compromise
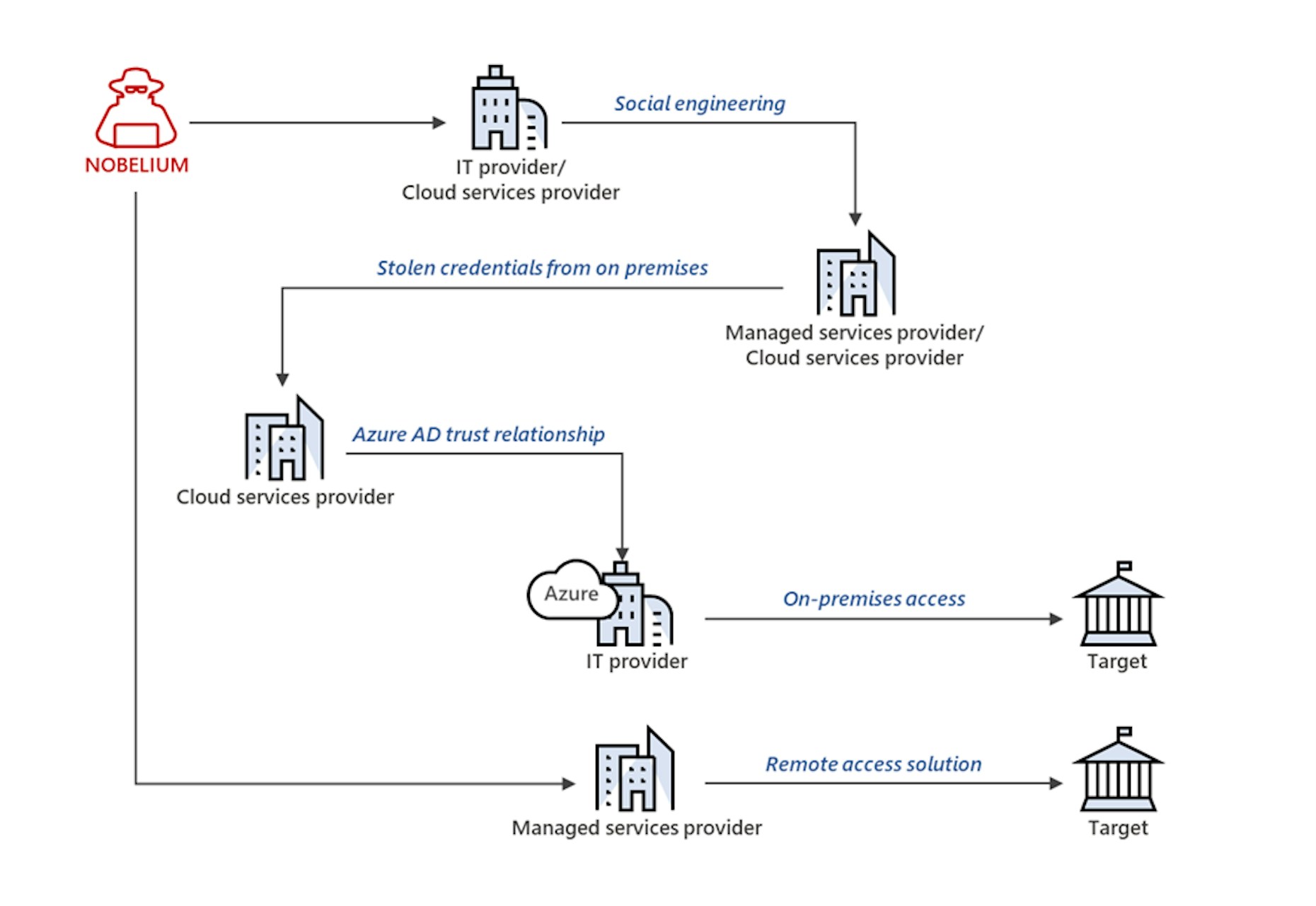
The threat actor behind the 2020 SolarWinds compromise, tracked by the Microsoft Threat Intelligence Center (MSTIC) as NOBELIUM, has been identified as attempting to gain access to customers using various cloud service providers (CSP), managed service providers, and IT service organizations.
According to MSTIC, NOBELIUM’s campaign attempts to exploit relationships between provider organizations and the “governments, think tanks, and other companies they serve.”
NOBELIUM uses malware, password sprays, supply chain attacks, token theft, API abuse, and spear phishing to access privileged accounts of service providers and move laterally in cloud environments. MSTIC notes that the lion’s share of compromise is the direct result of excessive and standing privileges.
“In the observed supply chain attacks, downstream customers of service providers and other organizations are also being targeted by NOBELIUM. In these provider/customer relationships, customers delegate administrative rights to the provider that enable the provider to manage the customer’s tenants as if they were an administrator within the customer’s organization.”
Permissions vs Flaw in Azure
MSTIC emphasizes that the attack is not due to a security vulnerability inside Azure. Instead, NOBELIUM uses its broad attack spectrum to exploit trust relationships among cloud providers and customers. These relationships are not unusual; CSP customers often grant standing privileged user permissions to various partners to accelerate business operations. The problem is that the permissions remain open and when targeted by a threat actor like NOBELIUM, present numerous opportunities to access admin controls and hijack entire workloads and environments.
Mitigation Steps – Investigate & Audit
Microsoft provides mitigation steps teams can follow depending on where they sit on the attack spectrum.
CSPs should verify and monitor compliance with Microsoft Partner Center, remove delegated administrative privileges, and conduct an investigation.
Downstream customers should review, audit, and minimize access privileges, verify multi-factor authentication (MFA) is enabled, and review audit logs.
Unfortunately, attacks like this are not going away. Increasingly, we see threat actors like NOBELIUM target CSPs and CSP customers using an array of tactics across broad attack surfaces. Once they breach your environment, it is difficult, costly, and time-consuming to mitigate the problem entirely. It is in an organization’s best interest to take a proactive stance by enforcing a Zero Trust policy through Least Privilege Access across all cloud environments.
How Britive can Help Reduce Your Privilege Blast Radius and Attack Surface
Here at Britive, it is stories like this that validate the critical nature of our multi-cloud privilege management platform. As Microsoft points out in its blog post, organizations should place priority on:
- Conducting regular user audits
- Granting Just-In-Time (JIT) permissions for all users
- Enforcing LPA cross-cloud
- Gaining complete visibility into user behavior
- Performing proactive monitoring for new attacks
With measures in place across all cloud environments, organizations can significantly reduce their attack surface and eliminate vulnerabilities due to excessive and standing privileges. NOBELIUM demonstrates the breadth and sophistication of today’s threat actors. Organizations must understand where they are at risk and take swift action to prevent serious harm to business operations, reputation, and security.
Regardless of where you are on your cloud journey, it is imperative to know which users – human and service IDs – have access to what and how to manage those privileges appropriately. The Britive platform is cloud-native and designed for speed and security. As part of your cloud security management, you will not have to worry about threat actors like NOBELIUM putting your success in jeopardy.




