


Back to resources
New Gartner Report: "Reduce Risk Through a Just-In-Time Approach to Privileged Access Management”
May 2022 / 4 min. read /

Privileged Access Management
A recent report issued by Gartner encourages organizations to employ a Just-In-Time (JIT) approach to improve privileged access management.
The report states:
Privileged access carries significant risk. Even with PAM tools in place, the residual risk of users with standing privileges remains high. IAM leaders must implement just-in-time strategies to pursue zero standing privileges.
JIT permissioning is based on granting temporary access to authenticated users only when it is necessary to complete tasks. When a task is finished, the access expires or revokes.
This means when a bad actor hacks an authenticated user account, the permissions needed to advance the breach do not exist.
Therefore, JIT permissioning has tremendous value for organizations seeking to develop products and services in the cloud:
- Developers have access to what they need, when they need it, and can meet business priorities by delivering products and services efficiently, without being slowed down by security.
- Security teams can dramatically reduce their attack surface by gaining control over who has access to what, when, and under which conditions.
Cloud security analysts also support JIT permissioning because it quickly helps eliminate the standing privileges often targeted by attackers.
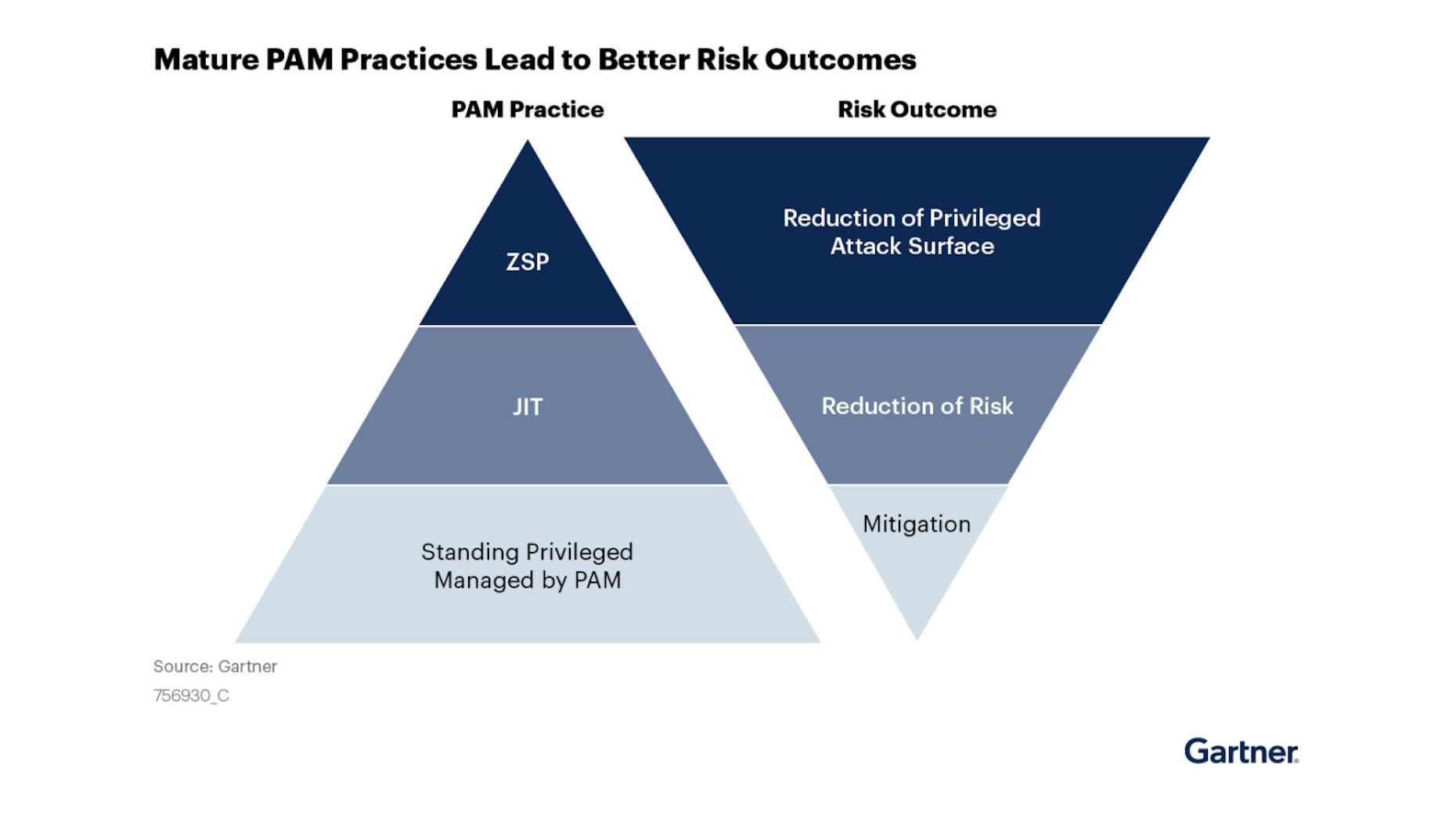
Standing and excessive privileges remain a critical flashpoint for organizations to resolve.
Just-in-Time permissioning helps businesses overcome the issue and move toward zero standing permissions (ZSP).
Gartner explains:
ZSP is the logical conclusion of JIT approaches, and represents a high level of maturity for a PAM practice. Under ZSP, not only are privileges made available only when needed, but they exist only when needed. While implementing JIT approaches will reduce the risk associated with privileged access, ZSP reduces the attack surface associated withstanding privileges. To move from JIT — which may still leave broad standing privileges —to ZSP requires more fully embracing the principle of least privilege and operationalizing administrative privileges to reduce the power any one account holds (thereby addressing the scope dimension of privilege risk).
Achieving ZSP through JIT permissioning is logical in theory, but what does it entail –– where can an organization begin?
Gartner suggests “targeting infrequent and already limited scope users, such as vendors and contractors, enables your team to cut its teeth on JIT approaches without wreaking havoc on a wide scale –– building both confidence in the new approaches and sufficient momentum to overcome potential objections from users more accustomed to broad, discretionary privilege grants.”
The figure below, provided by Gartner, shows the Five Ws of Privileged Access.
The goal is to determine who has access, when, to what, where, and why.
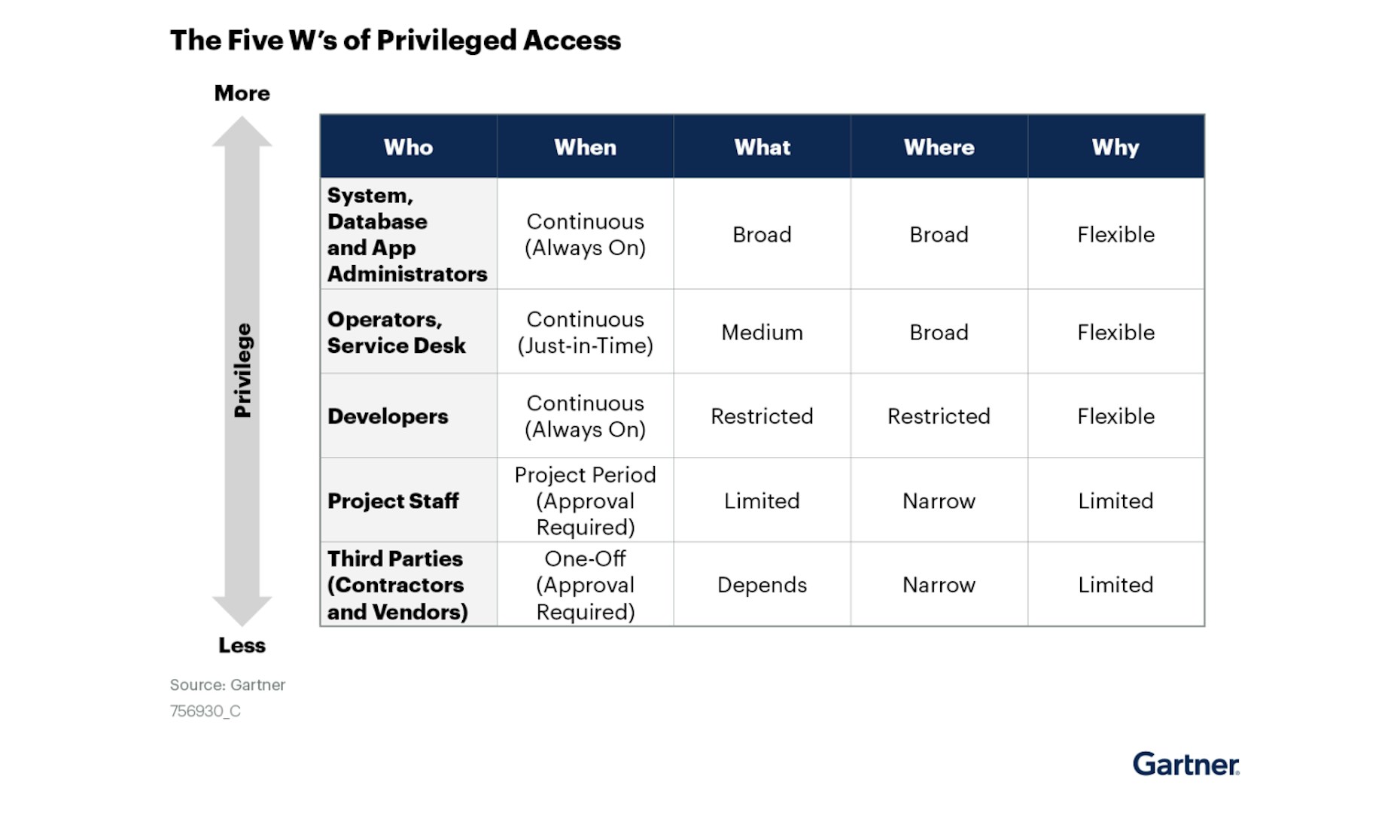
Identifying who has access to what is foundational to reducing the risks associated with privileged access. That is why it is essential to gain visibility across cloud environments and applications.
When privileged access instances are clear and understood, teams can make decisions that enforce cloud security best practices and accelerate business priorities.
Shifting to JIT permissioning pays dividends, but as an organization it is important to understand where your cloud journey is going and the strategy you will follow to get there.
Again, from Gartner:
Take a long-term view of JIT and ZSP. Not only will you need to move privileged workflows to JIT or ZSP gradually, but you are also likely to find gaps in the current capabilities of your existing PAM tools. Given the increasing maturity of ZSP capabilities among the tools in the market, it is worthwhile to inquire about feature roadmaps before seeking additional technology, and adjust your deployment plans and priorities accordingly. Push vendors to provide measurement tools that enable you to track progress against the metrics identified earlier as you migrate to JIT and ZSP across your environment.
Gartner's report concludes by encouraging organizations to review the Magic Quadrant for Privileged Access Management.
Go here to see where Britive’s dynamic permissioning platform sits on Gartner’s PAM maturity curve.

