
Identity security is undergoing major transformations. Legacy Privileged Access Management (PAM) based on vaults, and password rotation solutions are struggling to enforce security with the speed, agility, and dynamic scale necessary for the number of human, non-human, and even AI identities in the modern enterprises.
Zero Standing Privilege (ZSP) has emerged as the new standard for Identity Security. ZSP eliminates persistent, excessive and always-on access.
It grants users granular privileges they need, only when they need them, and only for as long as necessary. This proactive approach eliminates the risk of credential theft, insider threats, and lateral movement.
With a true ZSP model, organizations can secure identities and their interactions with business-critical applications and services. The ZSP model implements proactive risk prevention.
In the era of cloud, automation, dynamic environments and agentic AI, adopting Zero Standing Privilege becomes the cybersecurity enforcer rather than just an observer.
Before we dive in, lets quickly look at old PAM techniques and compare it with Britive modern identity security PAM with native API, without any proxy or agent.
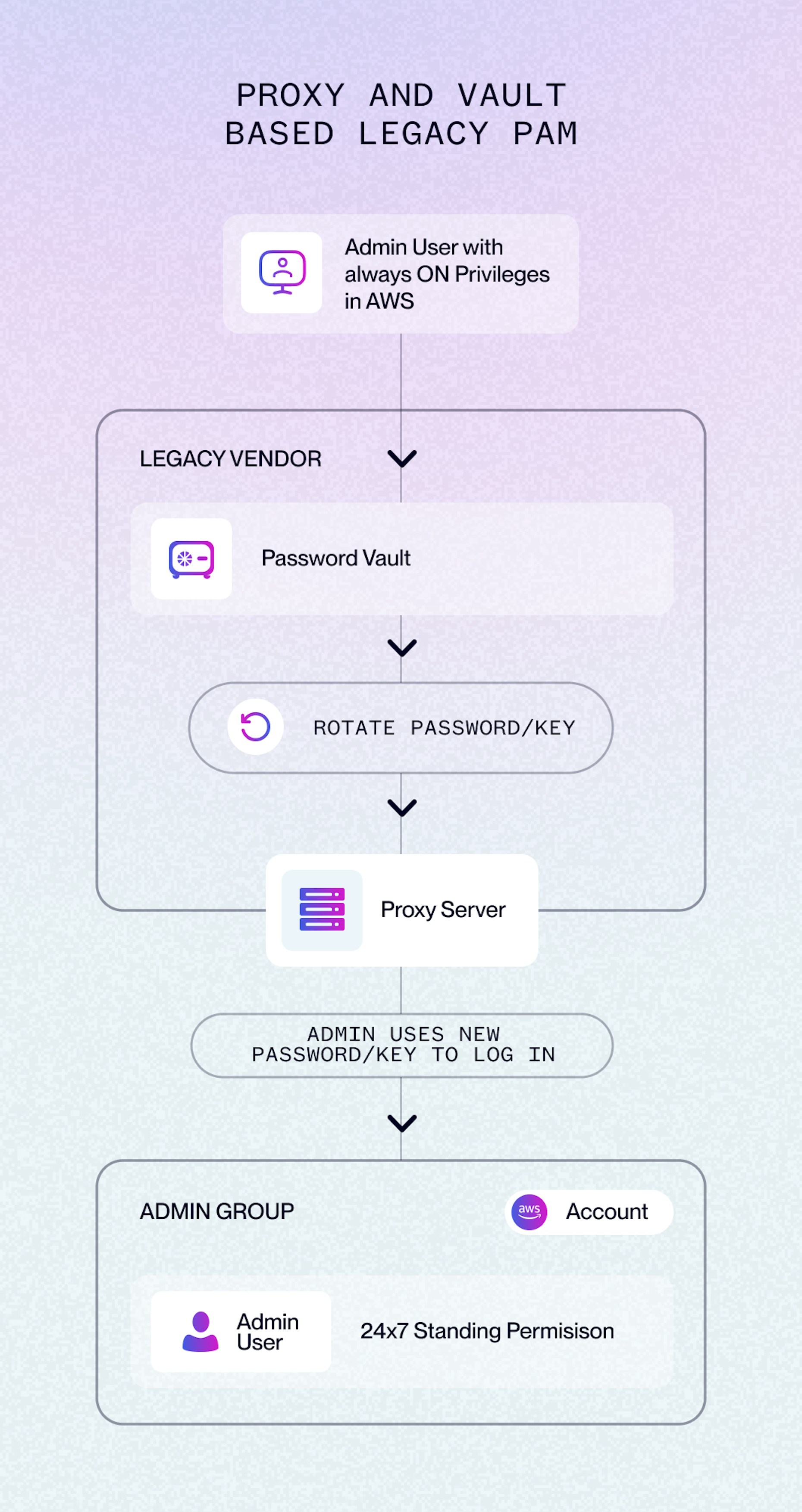
Legacy PAM: “Just-in-Time" Access with Standing Privileges
In the example diagram below, note its reliance on password rotations, secrets vaults and proxy-based access. Vault rotates the password or keys. A human then login to AWS account using the new password or rotated key. The permissions are "always on," and always accessible in AWS IAM.
Modern Identity Security PAM with True ZSP Implementation
True Zero Standing Privileges (ZSP) follows the Zero Trust security model. It makes sure no human or non-human (such as a computer program, service account, Agentic AI, etc.) has constant permissions or access to critical resources.
With True ZSP, the system or services don’t have any users or identities configured in the destination system or service. There are no permanently saved login details.
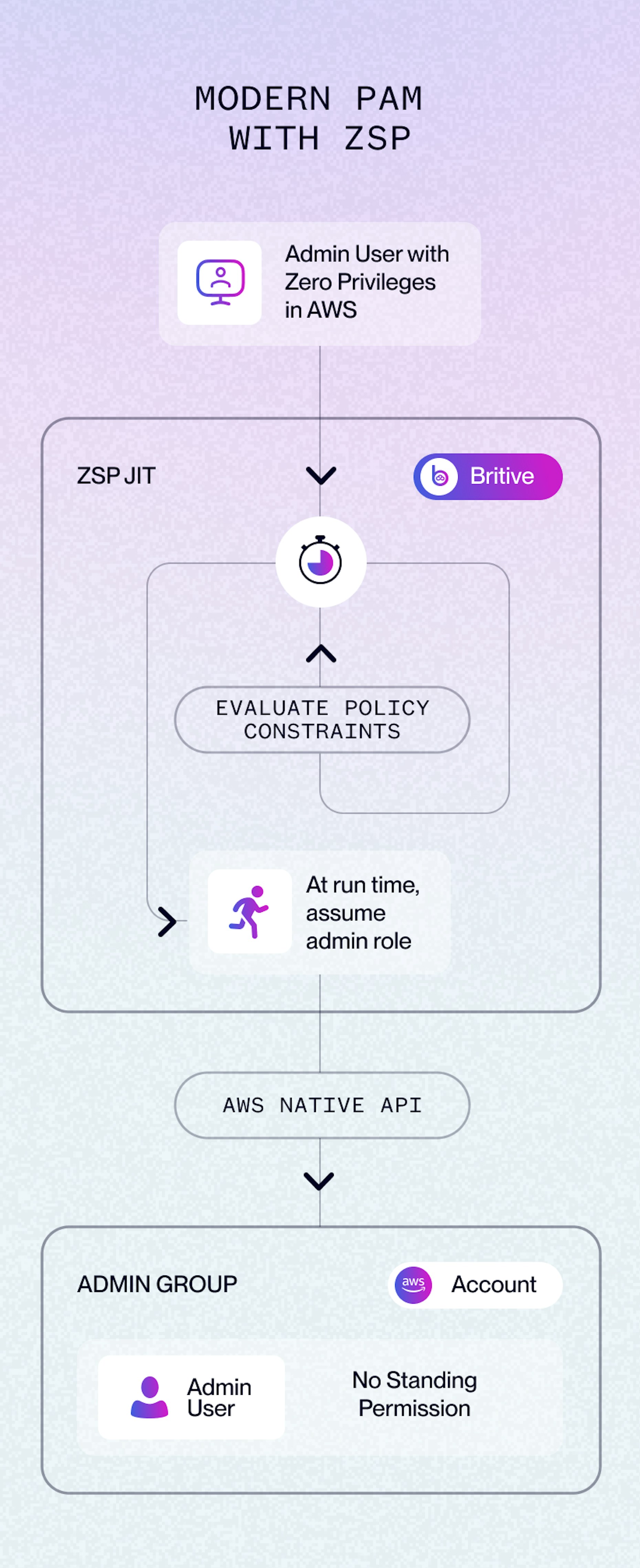
Zero Standing Privileges in Action: AWS Role Assumption Example
With true ZSP in AWS, you wouldn't find a user account like "AWS S3 Admin" as part of an AWS Group, set up with ongoing access. And because there's no permanent "AWS S3 Admin" account, there are no passwords or login details for that user lying around to be stolen or misused. Access is given only when needed, for just long enough to do the job.
With legacy vendors attempting to stay relevant and misuse the term "Zero Standing Privileges," it is essential to educate companies on what true ZSP should look like.
Zero Standing Privileges for Humans and Agentic AI
In a dynamic and ever scaling IT landscape, managing access for both human and non-human identities is a significant challenge. Traditional Privileged Access Management (PAM) solutions fall short in addressing the needs of modern cloud environments and AI-driven processes. Here’s why ZSP is crucial for Agentic AI and other non-human identities:
Reducing Attack Surface: This is particularly important for AI systems that often require elevated access to perform tasks but should not retain those privileges beyond the task's completion.
Enhancing Compliance: Regulatory requirements increasingly demand stringent access controls. ZSP helps organizations meet these requirements.
Improving Security Posture: With ZSP, organizations can enforce the principle of least privilege, ensuring that users and systems have only the access they need to perform their tasks, thereby reducing the risk of insider threats and external attacks.
Britive's AISP Approach to ZSP for Agentic AI Workflows
Britive is at the forefront of implementing ZSP for Agentic AI workflows. Our approach includes:
Just-in-Time (JIT) Access: Britive provides JIT access, granting permissions only when needed and for a limited time.
Granular Access Controls: With Britive, administrators can define highly granular controls, allowing precise permissions based on roles, environments, and tasks.
Continuous Monitoring and Auditing: Britive continuously monitors Agentic AI activity and audits every access request and action. This data can be exported to SIEM and SOAR platforms for real-time threat detection.
Automated Privilege Revocation: If a session ends or if a user’s access is revoked manually, Britive automatically terminates the session and removes entitlements, preventing extended access and ensuring strict compliance with Zero Trust principles.
Securing Agentic AI Workflows: Britive Example
As organizations adopt Agentic AI architectures, autonomous agents orchestrate complex tasks across various services. It becomes critical to secure the interactions between any non-human machine or AI identities.
Each stage of the AI workflow relies heavily on seamless, secure service-to-service communication. These NHIs are the invisible workers that fuel Gen AI pipelines, and without proper controls, they pose a significant attack surface.
This diagram illustrates a typical Gen AI ETL pipeline composed of four core stages:
- Data Ingestion (AWS S3 as example)
- Data Enrichment (AWS Glue as example)
- AI Model Training (Amazon SageMaker example)
- AI Model Inference (Amazon QuickSight example)
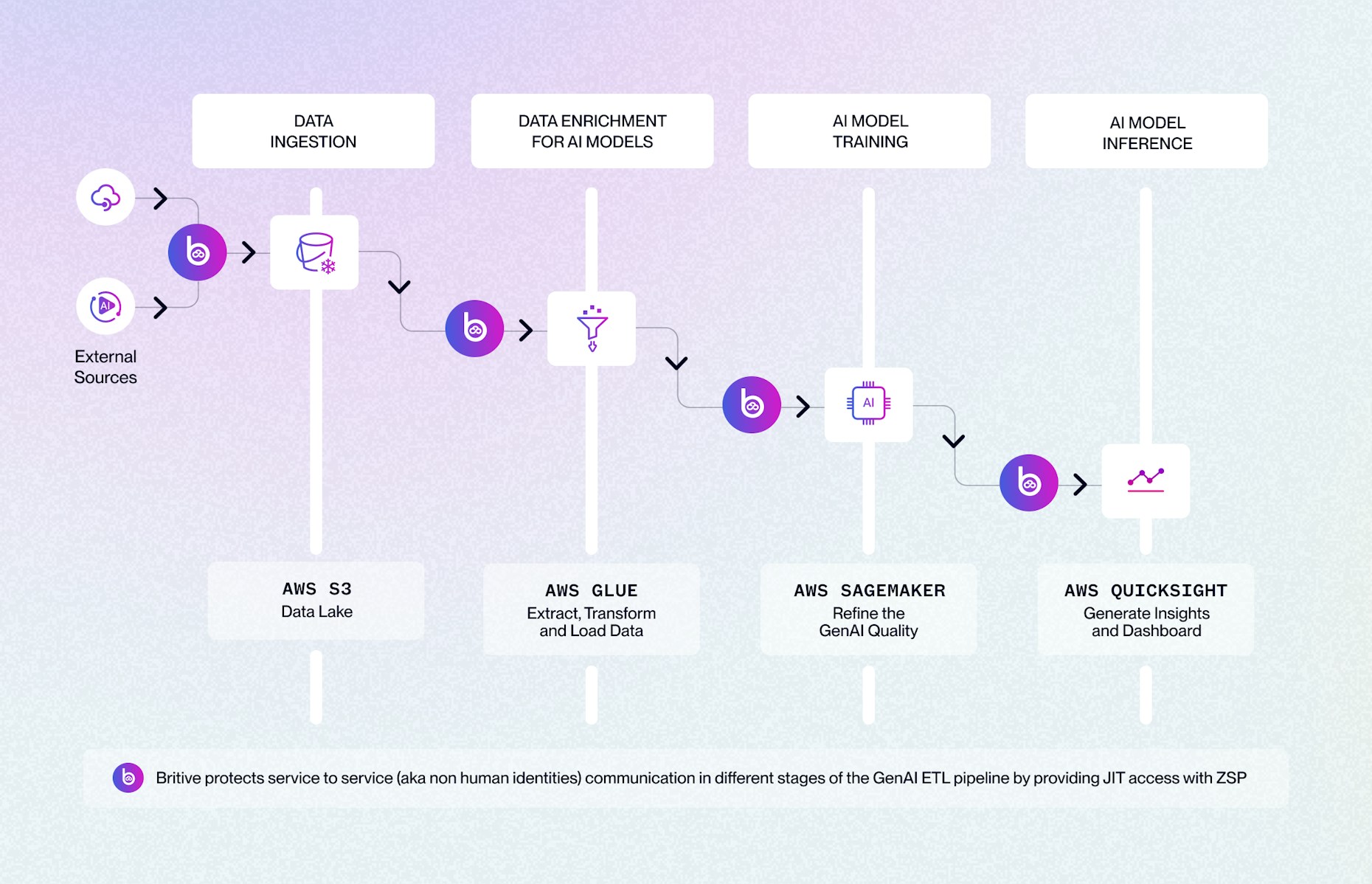
In this flow, NHIs are constantly accessing sensitive data, transforming it, training models, and visualizing results, all without human intervention. Each of these stages communicates with the next privilege access via API calls, IAM roles, or service accounts.
In the example let’s assume that an autonomous AI agent is managing a financial report for the shared holders based on varying market conditions:
- Financial data and signals are coming from different sources (internal and external) and saved in S3 data lake.
- When AWS Glue needs to pull the financial data from S3 and write to SageMaker, Britive grants a temporary token with only the permissions required just for the duration of the job.
- When SageMaker completes model training and needs to push results to QuickSight, another JIT access token is issued, scoped narrowly to prevent lateral movement.
- QuickSight auto-generates financial reports for financial analysts and decision-makers.
- These JIT entitlements expire immediately after the task is complete, leaving no attack window.
Why ZSP Matters for Agentic AI
Agentic AI agents can:
- Start and stop services as needed,
- Make decisions on their own,
- Work across different cloud and on-prem platforms.
If access controls aren’t flexible, these agents might get too many permissions, which is risky, or not enough access, which keeps them from working.
Britive addresses this risk this by:
- Giving agents only the access they need, right when they need it with patented JIT access and ephemeral permissions
- Automatically keeping detailed, auditable records of everything agents do, and
- Supporting both hybrid and multi-cloud setups for comprehensive visibility.
Britive’s approach follows the principles of Zero Trust security, always checking and adjusting what agents can do based on real-time context. This keeps systems secure, helps with audits, and makes sure organizations can use advanced AI safely and efficiently
Implementing true Zero Trust and JIT access allows enterprises to adopt and use AI safely. By making sure different services and agents can talk to each other, securely, temporarily, and visibly. As AI becomes more common and independent, protecting these connections is very important.





