Britive’s Multi-Cloud Privileged Access Management Platform helps Snowflake customers analyze and right-size cloud infrastructure privileges together with their security data lake
LOS ANGELES, Sept. 22, 2021 /PRNewswire/ — Britive, the cloud native, Multi-Cloud Privileged Access Management Platform, today announced a partnership with Snowflake, the Data Cloud company, to launch a ‘Bring Your Own Snowflake’ program. Joint customers can now normalize and analyze their IAM data for the purposes of obtaining insights into identity borne risks, recommendations for eliminating overly permissive access, and gaining visibility into access spread to allow automatic remediation of issues.
In addition, this model allows for the ingestion of historical identity and access data for analysis, as well as the enablement of users to proactively monitor their data for changes going forward.
“A 360-degree approach is key to effectively managing access permissions across cloud infrastructure,” said Omer Singer, Head of Cyber Security Strategy, Snowflake. “With Britive, Snowflake customers can now quickly gain insights into user permissions, actions and recommendations within the security data lake that they control.”
The Britive platform takes the complexity and time out of securing identities and permissions across multi-cloud environments, including IaaS, PaaS, SaaS, and DaaS services. The platform provides enterprise organizations with the ability to automatically grant Just-In-Time permissions, auto-expire permissions, enforce least-privilege access, right-size broad permissions and more.
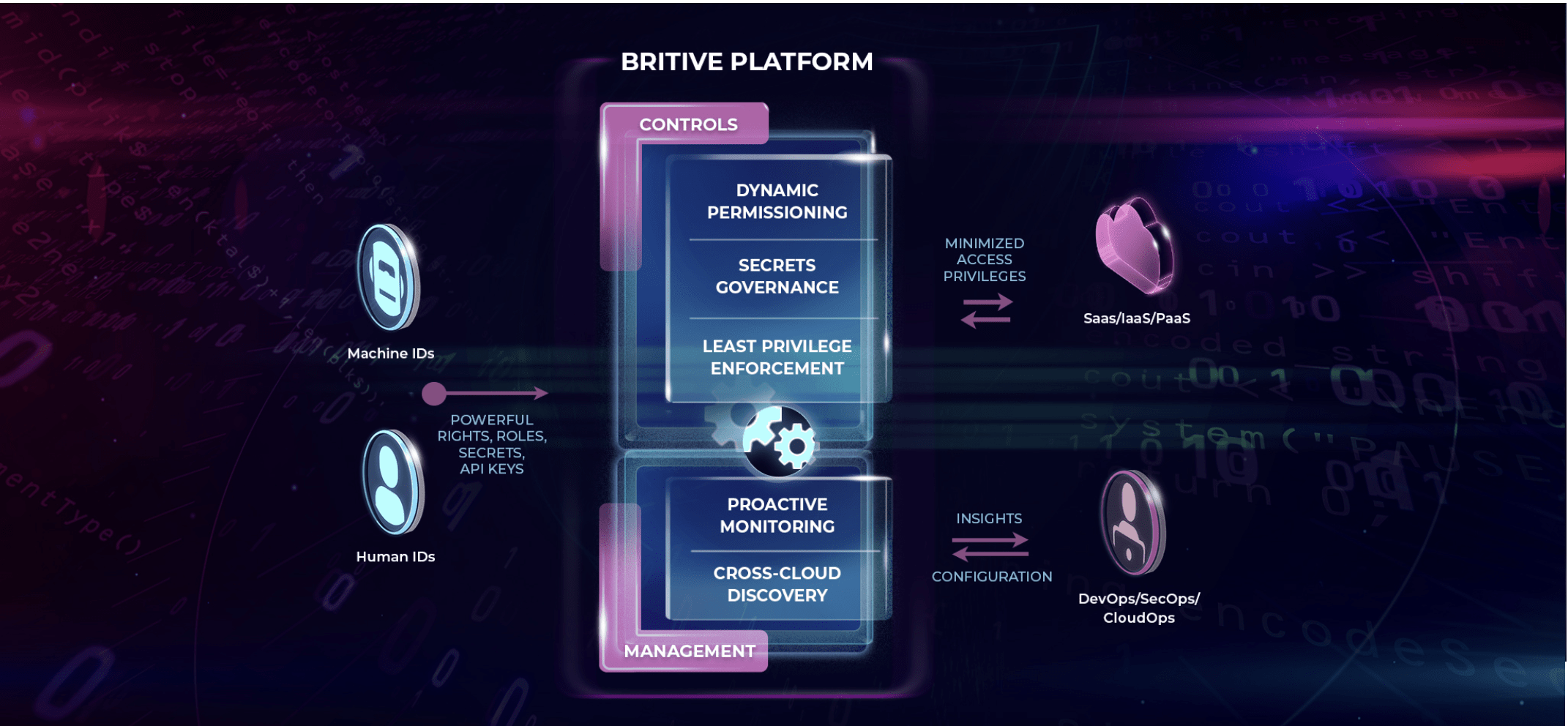
“As security teams increasingly rely on security data lakes to store and analyze their data, there’s now an opportunity to leverage that visibility to effectively analyze cross-cloud identity and activity,” said Art Poghosyan, CEO, Britive. “Britive is thrilled to partner with Snowflake to help our joint customers feel confident that their cloud user privileges are right-sized through continuous analysis, and access policies are automatically enforced as part of a modern security data lake architecture.”

