IBM Security and Ponemon Institute just released 2022’s “Cost of a Data Breach Report.” If you have not seen it yet, it contains some startling—but not surprising—statistics that are well worth your time.
Now in its 17th year, the report studied 550 organizations impacted by data breaches between March 2021 and March 2022. The breaches spanned 17 countries and 17 different industries.
At a high-level, the report confirms what we already know: the number of data breaches increases year-over year, breaches result in price increases that are passed on to customers, and nearly half of all the breaches cited in the report are cloud-based.
The report highlights that 83% of organizations studied have had more than one breach, and that the average cost of a data breach is a staggering $4.35M USD.
This presents a clear takeaway that all business and security leaders must acknowledge: data breaches are not a factor of “if” but “when” and the associated business interruptions and costs are potentially catastrophic.
Despite the dire situation, IBM Security provides strategic and tactical steps which can be implemented to reduce risk and lower the cost of a data breach.
Let’s take a closer look at some of the key findings.
How Zero Trust Reduces Breach Implications
Perhaps not surprisingly, the report recommends deploying a zero trust model for organizations operating in an on-prem, hybrid, or multi-cloud environment.
Zero trust is gaining widespread momentum. The White House released a memorandum in January 2022 stating that federal agencies must incorporate ZT-supported architecture by 2025. On the heels of the mandate, many organizations in the private sector appear to be recognizing the critical nature of ZT, particularly as it relates to cloud security, and taking steps toward implementing it in IT and Security architecture.
Zero trust’s holistic model for securing network, application, and data resources, with a focus on providing an identity-centric policy model for controlling access, aligns with security best practices and can quickly offset the attendant risks covered in IBM’s report.
There is a clear distinction between organizations that do and organizations that do not deploy zero trust: The report mentions that 59% of the organizations that were data breach victims do not deploy zero trust and needed an average of 277 days to identify and contain the breach.
Modern data breaches occur for the same reasons they always have: ransomware, phishing, and compromised credentials. It’s worth emphasizing, however, that stolen or compromised credentials tend to produce perilously high costs—up to $4.5M USD on average.
Compromised credentials can be so debilitating, especially in cloud and/or multi-cloud environments, because human and synthetic identities often have standing permissions and high-risk privileges that can give attackers access to cloud infrastructure and other operation-critical admin access.
Zero trust deployment eliminates implicit trust, meaning attackers lack the access needed to cause harm. But while implementing ZT across an organization may be a desired state, it is usually deployed in phases, often only realizing security needs once business imperatives are achieved.
The “Cost of a Data Breach Report” shows that when business imperatives—in this case, associated with software development— are aligned with Security in a DevSecOps fashion, the impact on the average total cost of a data breach drops more than $275,000 USD.
Moreover, since ZT is an identity-centric policy model, organizations that have proper Identity and Access Management tools applied to cloud environments see a $224,396 decrease in costs associated with a data breach.
Security Skills Shortage Breach Implications
Last but certainly not least, the report details how widespread security skills shortages can affect an organization when a breach occurs:
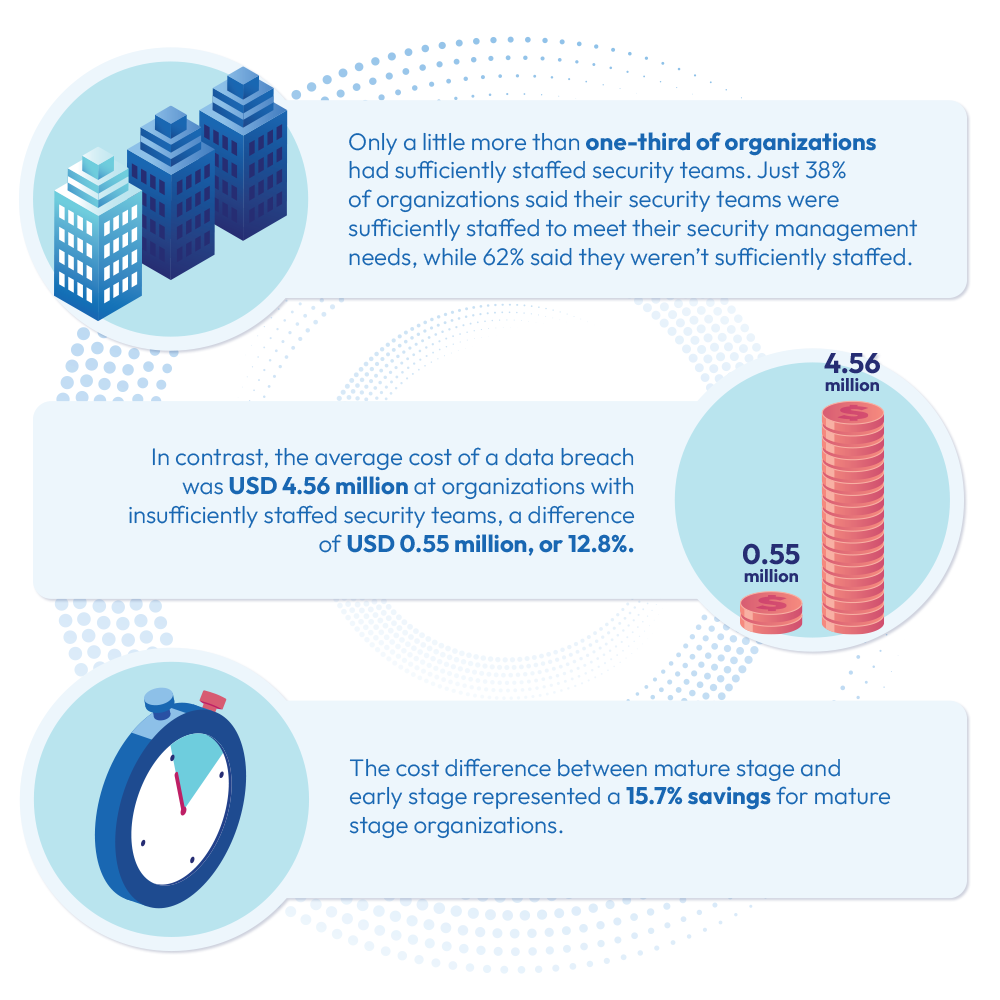
Since each cloud is different, with varying attack surfaces defended by a hodgepodge of native tools, multi-cloud organizations are particularly vulnerable to attacks. This is a painful reality as most companies move to multi-cloud to accelerate development, improve team collaboration, and facilitate key business drivers. But such growth, especially unchecked, leads to consequential risks. After all, most security experts have expertise in one cloud or another when what is needed is a unified access model to control and manage all identities across all cloud environments.
Conclusion
This is where Britive comes in. As a cloud-native platform designed to automate multi-cloud privilege identity management across data, infrastructure, and applications, Britive quickly eliminates the most pressing problems highlighted in IBM’s report. Here’s how:
Deploy just-in-Time permissioning
JIT access eliminates high-risk privileges and standing permissions by providing human and synthetic users temporary access to the services they need with the permissions they need. Transition from static privileges to an ephemeral, Just-In-Time access model to enhance the Time-to-Value of development cost and pipelines.
Gain cross-cloud visibility
See which users have access to which solutions across all your cloud environments. Cross-cloud visibility provides reporting into misconfigurations, high-risk permissions and unusual admin activity across SaaS, IaaS, PaaS and DaaS solutions so you identify risks sooner.
Eliminate privilege sprawl
With the adoption of multi-cloud, companies can be using hundreds or thousands of cloud services, which can generate thousands of data access events every day. This results in always-on human and synthetic identities and privileges that are vulnerable to exploitation.
Take control
Britive’s unified privilege access management dashboard delivers control and management through an all-in-one dashboard, filling the security gaps that put organizations at higher risk.
The IBM Security and Ponemon Institute report closes with a recommendation that validates Britive’s value and applicability.
“Adopt a zero trust security model to help prevent unauthorized access to sensitive data. Security tools that can share data between disparate systems and centralize data security operations can help security teams detect incidents across complex hybrid multi-cloud environments. You can gain deeper insights, mitigate risks and accelerate response with an open security platform that can advance your zero trust strategy. At the same time, you can use your existing investments while leaving your data where it is, helping your team become more efficient and collaborative.” –IBM Data Breach Report
If you’re serious about reducing risk and mitigating the cost of a breach, contact us today. We’ll have a customer success professional ready to answer all your questions.

