Gartner notes that “vendors such as … Britive … combine dynamic secrets, authentication, authorization, and just-in-time credentials to enforce least privilege access to service and resources.”
Attacks designed to disrupt software supply chains are growing in scope and sophistication.
According to the recent Gartner report, “How Software Engineering Leaders Can Mitigate Software Supply Chain Risks,” the time for software engineering leaders to take action is now.
Gartner states that software engineering leaders “are at the forefront of digital business innovation” and must not only develop and deliver software but also implement security practices that protect the supply chain. Traditionally, these security practices have included scanning code for vulnerabilities and patching software systems. But Gartner says more robust measures must be applied.
Attacks targeting software development systems, open-source artifacts, and DevOps pipelines are occurring with greater frequency.
As we have seen with SolarWinds, NetBeans IDE, Kaseya, and Codecov, these attacks prey on continuous integration/continuous delivery (CI/CD) systems, inject malware into legitimate software, and install vulnerable and malicious dependencies whenever possible. As a result, Gartner assumes that by 2025, “45% of organizations worldwide will have experienced attacks on their software supply chains, a three-fold increase from 2021.”
The report shares three principal conclusions:
- The increased threats of malicious code injection make it critical to protect internal code and external dependencies (both open-source and commercial).
- Leaked secrets or other sensitive data and code tampering prior to release are consequences of a compromised software build and delivery pipeline.
- Failure to enforce least privilege environments and flat network architectures enables attackers to move laterally against the operating environment, putting the enterprise at greater risk.
Given the many opportunities to exploit externally sourced and internally developed code, Gartner states that software engineering teams should assume all code has been compromised. They recommend software teams work closely with security and risk partners to develop strategies to defend the supply chain.
Organizations may not be able to stop the threat of malicious code injection, but when supported by Britive’s platform, can address the risk of protecting secrets and least privilege enforcement.
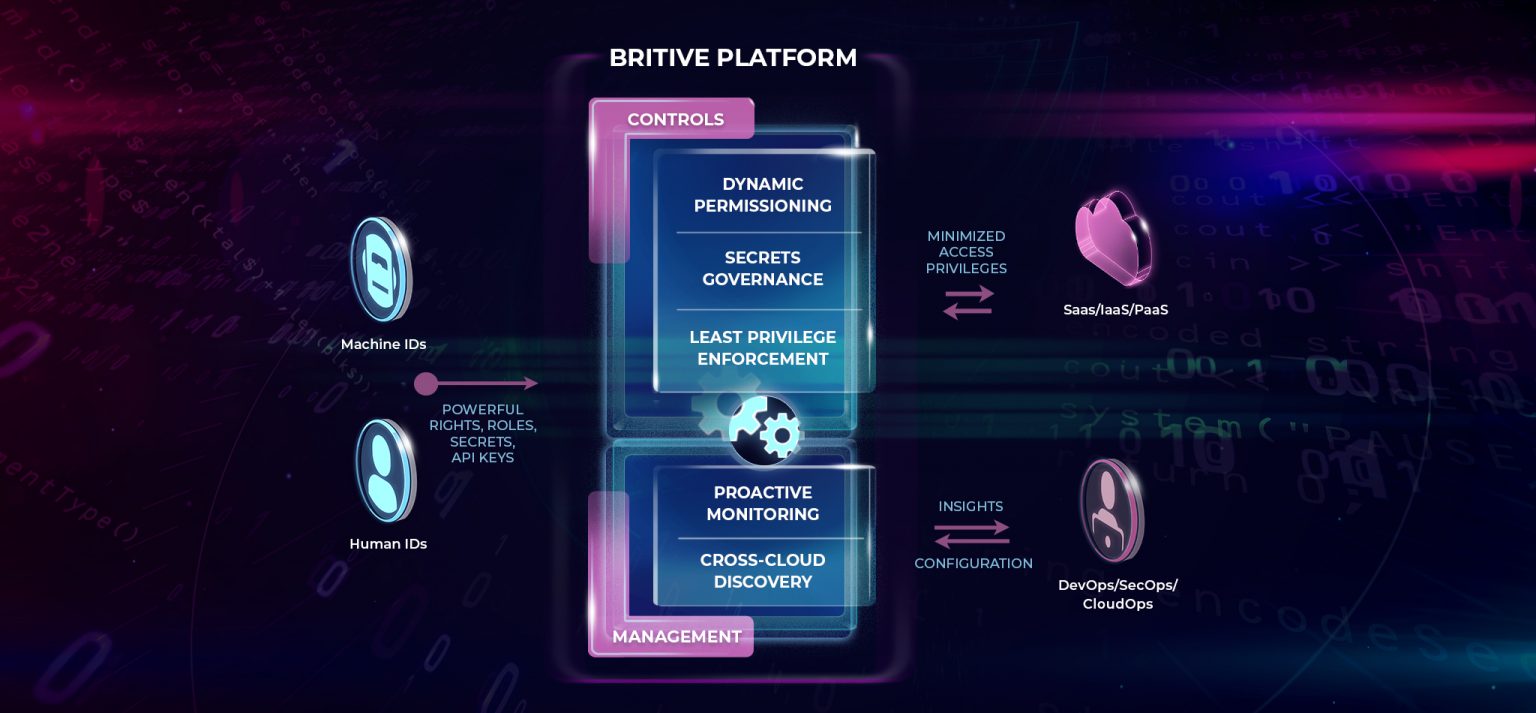
Just In Time (JIT) secrets can be granted and revoked on the fly, which is ideal when DevSecOps needs to spin up temporary services. Teams can automatically grant and expire secrets, rotate passwords when users leave the organization, and investigate who has access to which secrets.
Britive also empowers DevSecOps to enforce least privilege access and minimize the attack surface.
Teams can right-size overly broad permissions and eliminate excess privileges. Collectively, these measures significantly reduce the privilege attack surface. As a result, hijacking over-privileged accounts or stealing static API keys becomes a thing of the past.
Additionally, Gartner recommends:
- Protecting the integrity of internal and external code by enforcing strong version-control policies, using artifact repositories for trusted content, and managing vendor risk throughout the delivery life cycle.
- Hardening the software delivery pipeline by configuring security controls in CI/CD tools, securing secrets, and signing code and container images.
- Securing the operating environment for software engineers by governing access to resources using principles of least privilege and a zero-trust security model.
The strategy Gartner recommends here aligns with Britive’s commitment to securing privileged access to cloud development environments. A software engineering team’s primary focus is developing and delivering software, not administering security systems; however, the threats to software supply chains are real and require diligent monitoring and mitigation.
Preserving code integrity, insulating the delivery pipeline, and securing operating environments is essential but can be a challenge to implement. Software and security teams must coalesce to ensure supply chain threats do not impede business operations and growth.
How does Gartner recommend teams achieve this?
Let’s break down the three points for context.
Protect the Integrity of Internal and External Code
Version Control Systems (VCSs) and artifact repositories need strictly enforced security controls to protect internally developed code and external artifacts. Without tight controls, source code and artifacts are at risk for malicious exposure.
Gartner recommends a.) using strong version control policies, b.) relying on trusted component registries, and c.) implementing appropriate third-party risk management.
Harden the Software Development and Delivery Pipeline
Bad actors look to exploit vulnerabilities at every stage in the software procurement, development, and delivery lifecycle. The report quotes Steve McConnell: “In software, the chain isn’t as strong as its weakest link; it’s as weak as all the weak links multiplied together.”
As a result, Gartner recommends a.) implementing secrets management, b.) implementing signing and hashing to verify the integrity of source code, and c.) configuring security controls in CI/CD pipelines.
Secure the Operating Environment for Developers
The rapid shift to multi-cloud environments means software departments increasingly rely on a composite of tools and platforms to exchange information and propel development. Vast numbers of users may comprise these privileged service accounts, making it difficult to evaluate, control, and revoke elevated privileges.
Here at Britive, we know that by 2023, “75% of security failures will result from inadequate management of identities, access, and privileges.”
Gartner recommends employing Zero-Trust Network Access (ZTNA) and Privileged Access Management (PAM) tools. ZTNA reduces the identity and access surface area where supply chain attacks occur, while PAMs monitor the DevOps privileged accounts typically responsible for running builds and controlling automation.
The authors note that “vendors such as … Britive … combine dynamic secrets, authentication, authorization, and just-in-time credentials to enforce least privilege access to service and resources.”
The message this Gartner report imparts is clear: the nature of software supply chain attacks is growing in scope and sophistication. Open-source packages injected with malicious code, back doors installed in post-deployment updates, third-party weaknesses exploited – these risks and others are a potential perfect storm for software teams.
But by following the recommendations above, and working closely with security partners, software engineering leaders can effectively mitigate supply chain risks.

