Policy-Driven Workflow Approvals
As part of our continued effort to bridge the gap between privileged access management and business objectives in the cloud, we are excited to announce this important new feature of Britive’s Dynamic Permissionsing Platform.
Here’s how it works:
Leverage Just-In-Time (JIT) permissioning capabilities to approve or reject privilege access requests by users in your organization. The workflow approval process is determined by security policies established within your organization.
This is beneficial for two important reasons:
- Policy-based access control empowers your team by enforcing PAM best practices
- JIT capabilities ensure team members have access when they need it, but eliminates standing privileges that are subject to attack
Let’s take a deeper look.
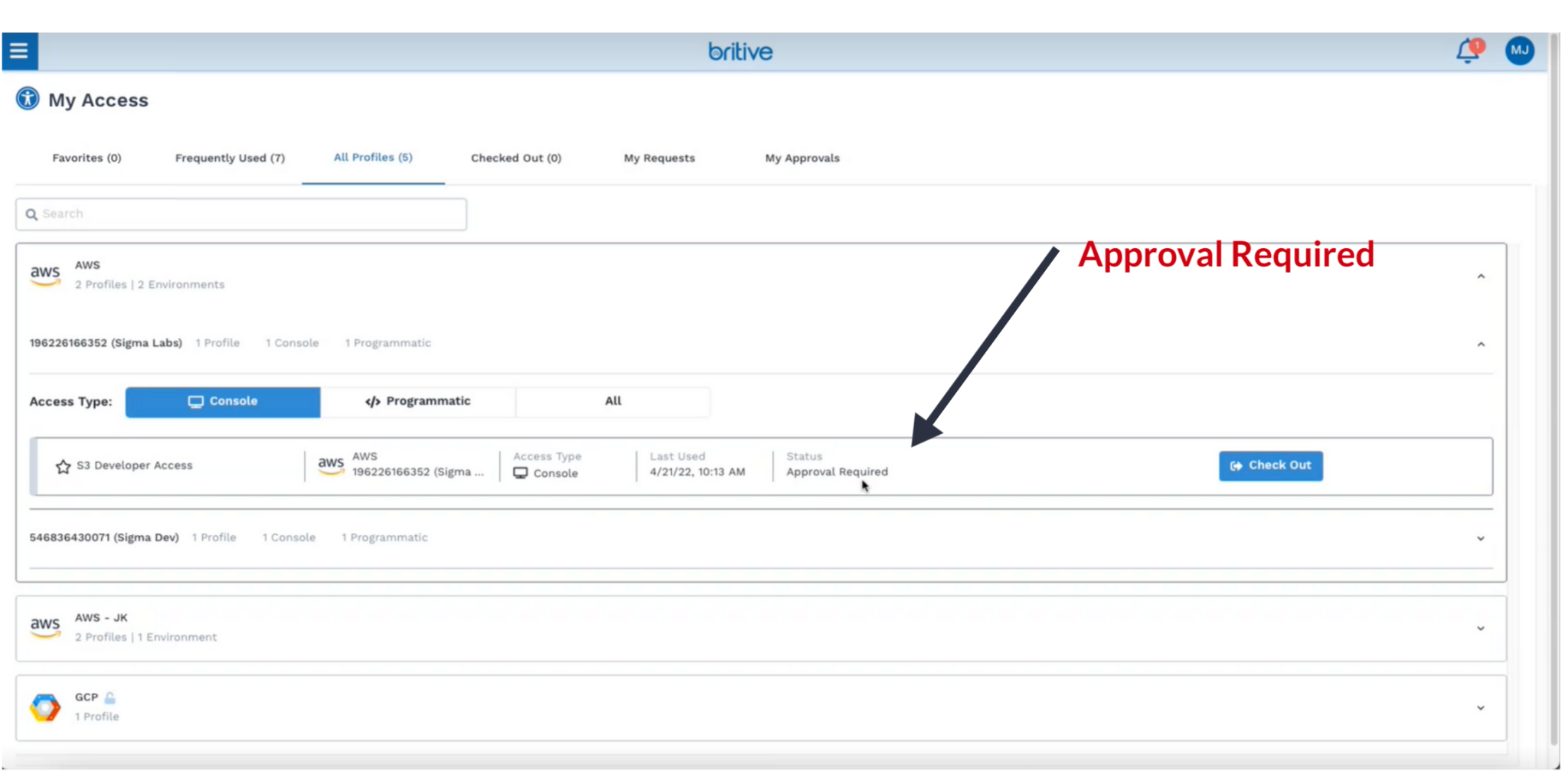
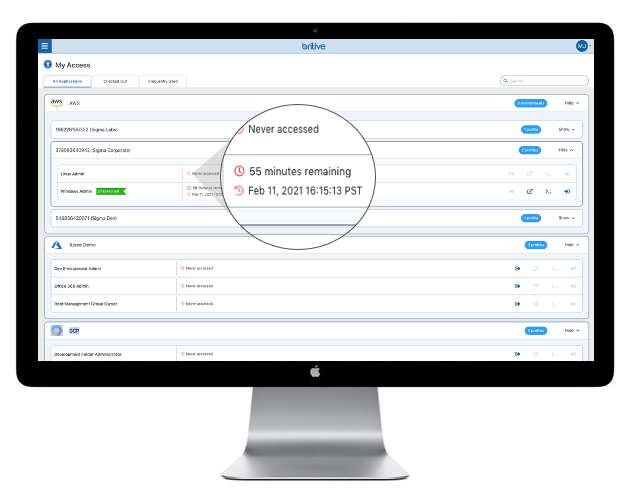
In this demo shot, we see the Britive console, where a user is attempting to access an organization’s AWS environment.
- User “Mary Jones” works on the Help Desk, which is shown as part of her profile
- Mary needs S3 Developer access in AWS
- The organization’s security policy states that as a member of the Help Desk group, Mary’s request must be approved by an Admin
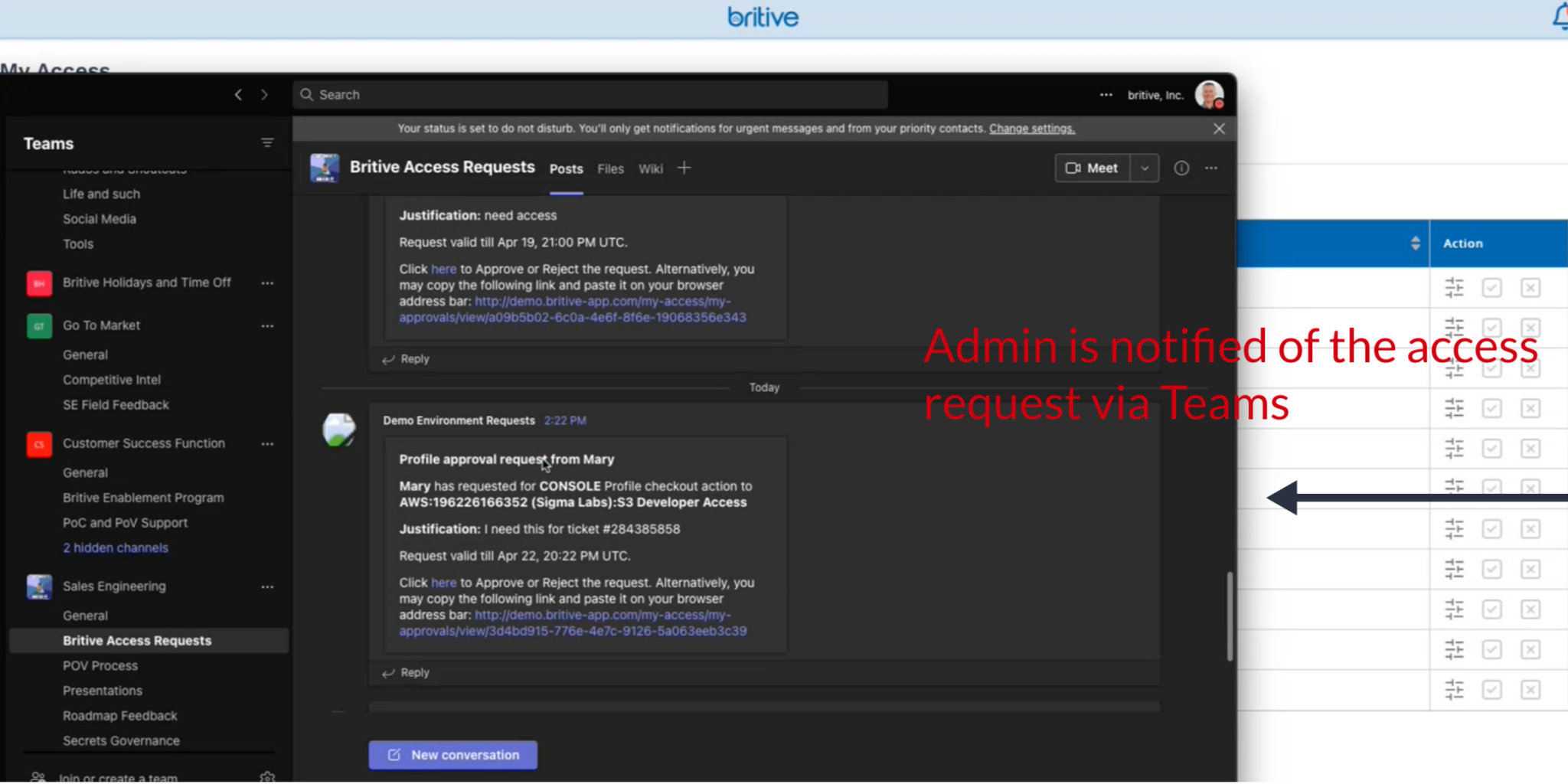
When Mary sends the request, the Admin is notified immediately.
- Mary sends her request to an Admin
- The Admin receives the request via email, Teams, or any other connected medium
- The Admin reviews Mary’s request and approves or rejects it based on policy
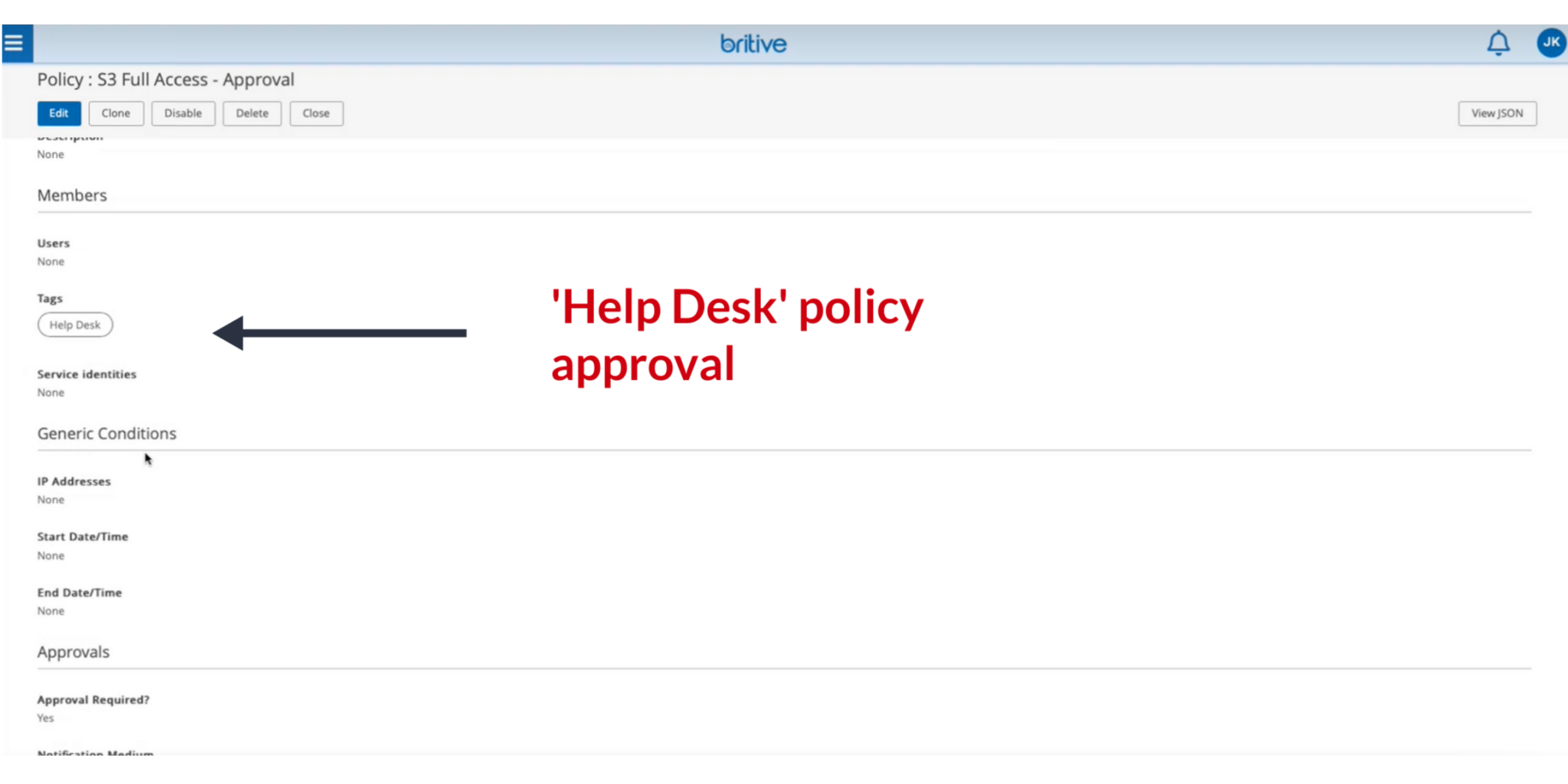
This shot shows the policy page that gives the Admin context to approve or reject the access request.
- Policy has established that a Help Desk user needs this workflow approval
- Policy has also established that Admins do not need permission –– they have automatic access
- When the Admin approves Mary’s request, she receives access for 59 minutes (or for a duration of time your organization dictates)
- When Mary’s session expires, her access is revoked. Alternatively, if Mary completes her task before the allotted time expires, she can “checkout” the access and then it is revoked
Let’s recap. In this post’s example, an organization’s policy-based access control says that Help Desk users need approval for AWS S3 Developer access.
Policy also states that Admins do not need approval – they have access to what they need and are responsible for approving or rejecting Help Desk requests.
Workflow Approvals
The new feature lets you establish strong policies based on cloud security best practices without impeding workflows.
- High-level privileges are protected
- Users follow request access as part of their workflows
- Access is granted or denied based on policy
- Access is revoked when the task is complete
- Standing privileges are eliminated
Organizations can create various policies based on which teams may need access to specific environments. One policy may determine who can access what, and when, for your Security team. Another policy can be created for the Engineering team, etc.
Britive’s Policy-Driven Profile Workflow Approvals leverage the security and agility of JIT permissioning. The feature can be implemented across every cloud environment Britive supports – IaaS, PaaS, SaaS, and DaaS.